
What Is Firewall Protection?
For website owners who want serious security without the hassle of managing their own firewall, dedicated firewall hosting can provide real-time monitoring and protection. This is paramount for sensitive data and to reduce or even prevent Denial-of-Service (DoS) and other attacks.
What Is a Firewall?

In short, a firewall is a security system for your network. It can either be hardware-based or software-based. Basically, a firewall uses rules which help it control inbound and outbound traffic to a computer.
As it sounds, a firewall is a barrier between the trusted network that your computer is on and the untrusted network of the rest of the internet. A firewall will deny access to the trusted network by traffic that isn’t defined in the firewall policy.
History of Firewall Protection

Firewall and switches. Image courtesy of Karri Hutanen/Flickr
Firewalls didn’t emerge until the 1980s when it became important to control access to servers. Up until then, routers running access control lists were the only form of network security that could grant or deny IP address access to the network.
Connectivity and networks increased massively with the introduction of the internet. So this basic access control list filtering wasn’t enough to prevent malicious attacks on computers and servers.
The first commercial firewall was shipped by Digital Equipment Corp. in 1992. Since then, firewall technology has evolved immensely.
What Are Ports?
A port is a virtual point of connection that your computer uses to connect to the internet or other computers. For example, a program on your computer will connect to the internet via a specific port number.
Port Numbers
Ports let your computer determine what kind of data is requesting access to it. For example, is it the World Wide Web? Is it e-mail? DNS? Fire transfer? They determine the nature of the incoming traffic to your computer.
Port numbers have been universally assigned to different internet services based on a general consensus among users. Firewalls work by blocking access to many of your ports.
Firewalls And Ports
Most people won’t have to configure the ports on their firewall. Firewall software will simply ask you if you want to allow certain applications through. Though, sometimes you may have to enter your firewall settings to open certain ports if applications are being blocked.
A TCP port (Transmission Control Protocol) is used for transmitting data based on a connection. Computers transferring data connect directly to each other through this port.
This allows for a secure connection between the two computers. This port should be allowed to be open by most firewall software by default. It is required for all incoming and outgoing communication.

The Various Types of Firewalls
The first firewalls were packet filters. These firewalls checked packets that were sent between computers and made sure that the specifications of the source and destination address were allowed onto the network by the firewall’s rules.
Stateful Firewalls
Stateful firewalls added to this early technology by speeding up processing. Instead of checking each packet in isolation against the rules of the firewall, stateful firewalls recognize packets of an existing connection so they can be allowed into the network without having to be checked individually.
Application Layer and Proxy Server Firewalls
Application-layer firewalls were developed to protect servers and their applications. These firewalls block specific content, like malware, from accessing the server.
Firewall proxy servers are similar. These also operate to protect the applications on a server. A proxy server prevents direct connections between both sides of the firewall. Instead, computers and servers have to run through the proxy first, which has a rule set for blocking or allowing traffic through.
Host-Based Firewalls vs Network-Based Firewalls
Let’s compare two types of main firewalls, which are host-based or network-based.
| Firewall type | Installation location | Malleability |
|---|---|---|
| Host-Based Firewall | Installed on each individual server or computer | Incredibly flexible – VMs and apps can be moved along with their host-based firewalls |
| Network Firewall | Installed at the network level | Easily scalable, should bandwidth demands increase |
Host-based Firewall
A host-based firewall controls incoming and outgoing network traffic and determines if it’s allowed the particular device. Virtual machines can be moved, taking their host-based firewalls with them. Each device on a network can be configured with custom firewall rules.
Mobile computers (such as laptops) have the protection of a firewall wherever they are.
A host-based firewall also prevents attacks from within a network.
Network Firewalls
Network firewalls function on the network level rather than the individual computer level. This firewall filters data as soon as it enters the network before it reaches computers on the network.
A network firewall is the first line of defense for networks.
An advantage of a network firewall is that it may route traffic through a proxy server. The downside is that hardware firewalls require monitoring and management which may be complicated.

Hardware, Software, and Cloud Firewalls
Both hardware and software firewall solutions are designed to prevent unauthorized connections to servers and computers. Another more modern option is cloud firewalls. These cloud firewalls involve on-site hardware with remotely-managed software interfaces.
This software can be managed by certified security professionals in a different geographic location. Companies like this because they don’t need on-site management of the firewall.
Software Firewalls
Firewall software is installed on computers to protect them from attacks directly. Software firewalls are also called host-based firewalls. If you run a business in an office with a large network of employee computers, you would need to install firewall software on each one to protect them.
This may be expensive if you’re purchasing firewall software, and also means that everyone in the office needs to know how to allow applications through and keep the firewall updated.
Hardware Firewalls
On the other hand, hardware firewall products will protect all computers on the same network. This is the ideal solution for small businesses. These hardware firewalls can be purchased as a product.
Often, they are included in broadband routers. Chances are, you have a hardware firewall in the router in your home. So, every computer connected to the local network via this router will have firewall protection.
Your Home Router Has a Firewall

The hardware in your router works like this. Your home router shares a single IP address from your ISP with the network of computers in your house that are connected to the router.
Incoming traffic from the internet reaches your router’s single IP address. So your router doesn’t know which computer it should send the traffic to and it simply doesn’t send it anywhere.
As a result, the firewall in your router prevents incoming traffic to your computers. This effectively blocks unrequested traffic from reaching computers on your local network. You may be able to configure some hardware firewalls to block forms of outgoing traffic as well.
Bastion Hosts and DMZ
You can set up a DMZ (demilitarized zone) to forward all of this incoming traffic to. This is a computer that would receive all of the incoming traffic on your router. Some people set this up to draw attacks, in order to determine and trace the source of these attacks.
Bastion Hosts
Computers set up in a DMZ will be completely exposed to attacks. Computers can also be set up outside of a firewall. Either way, these exposed computers are called bastion hosts. They are designed to withstand attacks.
They are deliberately exposed to the public network because they act as a gateway for attacks, connecting the secure network and the insecure network together. For example, e-mail servers and FTP servers are typically bastion hosts. Bastion hosts are kept secure by only keeping one application on them.
Bastion Hosts and the DMZ Work Together
Hardware firewalls and routers themselves can be considered bastion hosts. In larger networks, a bastion host is placed in a DMZ between two firewalls. On smaller networks, the bastion host would sit outside of the single firewall.
The purpose of separating servers like e-mail, FTP, and DNS is because these hosts provide services to users that are outside of the LAN (local area network). As a result, it’s more likely that these servers will be attacked.
They are placed outside of the protected network to keep the rest of the network safe from attacks.
Which Type of Firewall is Best?
The hardware firewall included in your internet router is fairly secure. Many people ask whether you also need to have firewall software installed on individual computers as well.
Use Both Hardware and Software Firewalls
Most businesses and homes use both types of firewalls. So, if a virus gets access to the network, it doesn’t automatically affect every computer on that network. Each computer’s host-based firewall will filter the threat itself. Using both software and hardware firewalls on your network will provide the best protection for computers against attacks.
Sharing a Secured Network over VPN
Larger companies may use a site-to-site VPN to connect offices in multiple locations on the same network. As a result, multiple different geographical locations can be connected. This allows larger companies to share a secured network.
Looking for a great deal on secure hosting?
SiteGround – rated #1 by our readers – provides advanced security, including AI-powered proprietary systems that they developed in-house. Right now you can save up to 67% on their quality plans. Use this discount link to get special pricing.
What Firewalls Don’t Protect Your From
Firewalls filter through incoming traffic and block traffic that is unauthorized.
Firewalls are great, but you can’t rely on them to protect you from everything. There are still many security threats that your computer will experience which a firewall cannot block.
Beware of Malware
Malware can still find its way onto your computer if you click on malicious e-mail attachments or links. This is because firewalls do not block e-mails as e-mail servers are usually outside of the firewall.
Malware Opens the Gate
Once these emails are on your system, they have made it passed your network firewall. These kinds of threats can come in the form of trojan horses, viruses, spyware, adware, and phishing.
Some firewall software may be better able to protect you from these kinds of attacks. But it’s also good to understand the possible security threats that you may encounter when using the internet. Your first defense against malicious e-mails is being able to recognize them.

Windows Firewall
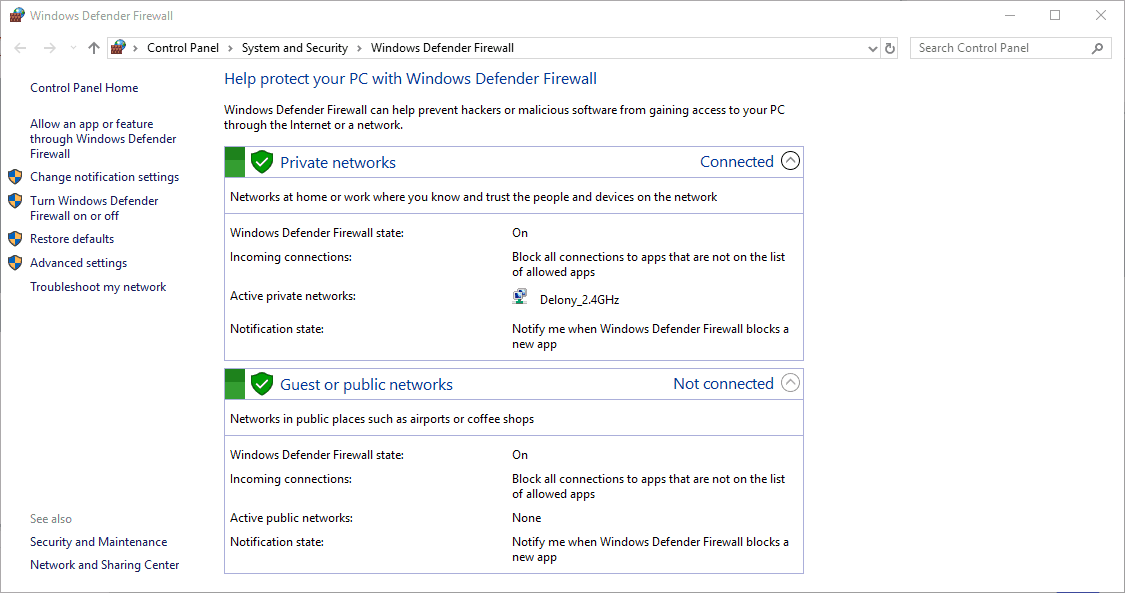
Every Windows operating system comes with its own firewall. Any Windows computer will have this by default. The Windows firewall does everything that third-party firewall software will do.
How Windows Firewall Works
It blocks incoming connections that it hasn’t authorized. This is why Windows users will sometimes receive a pop-up when they open a new application for the first time.
This notifies users that the Windows firewall is blocking some features of the program and gives you the power to allow it access to your network or deny access if you don’t recognize it.
Should You Use Third-Pary Firewalls?
There are a lot of third-party firewall software options out there. These may expand upon the functionality of the default Windows firewall, though most computers won’t need more than Windows provides.
ZoneAlarm
The Windows firewall interface isn’t super user-friendly, so it may be hard to find their advanced features.
One popular third-party host-based firewall is ZoneAlarm. This is one of the best free firewall options available. If you’re looking for a free firewall download, give it a try.
ZoneAlarm hides your open ports, identifies unauthorized traffic, and disables programs that may be malicious. ZoneAlarm will also protect your computer when it’s connected to public Wi-Fi.
GlassWire
Another useful firewall is GlassWire. This firewall software will let you know a list of the programs that are receiving and sending data over the local network. This will make it easy for users to spot unusual activity. GlassWire makes it simple to block programs from gaining internet access and keeps you aware of security information.
Firewall Software for Servers
Much paid security software for servers also includes a firewall with it. For example, Mcafee Host Intrusion Prevention and Symantec Endpoint Protection.
Symantec Intrusion Protection
Symantec Endpoint Protection is a paid suite of security software. It includes anti-malware, intrusion protection, and firewall features. This software is usually installed on servers or desktop computers.
Likewise, McAfee Host Intrusion Prevention is also meant to defend servers. This software will secure servers against malicious attacks using a dynamic firewall.
Should You Use Paid Software?
People using dedicated servers that don’t come with their own firewall may want to consider paid software such as these to protect them. Since dedicated servers give users all the control and responsibility for the hardware, you’ll likely have to take care of security concerns yourself.
This is one of the many reasons that dedicated servers should only be used by people who know what they’re doing or have a server admin to take care of things.

FTP Access and Firewall Security
Many developers use FTP (file transfer protocol) to access website files on the hosted server. Popular FTP software includes Filezilla, which is, in fact, free to use.
FTP Access and Open Ports
They need this access to manage, upload and edit files. This may be important for web design or security processes. FTP poses some security challenges to firewalls.
Depending on your FTP client, you may have to leave some ports open. This makes them available to unrequested connections from unauthorized inbound traffic.
Why You Need a Firewall for Your Website
Now you’re familiar with firewalls, the hardware and software systems designed to protect your computer and the information flowing to and from it from prying eyes and malicious attacks.
Protecting Sensitive Data
The same principle applies when it comes to your website. Most content needs to be monitored and defended from less savory denizens of the electronic ether. These include content for visitors such as:
- Multimedia content
- Blogs
- Online Shops
Furthermore, the information they submit to your site like:
- Credit card numbers
- Purchase histories
- Any correspondence
You May Need Stronger Security
For many website owners (particularly those using shared hosting), a passive or self-managed firewall solution may not be enough.
The same level of technology you rely on at home to keep your WiFi secure may not be up to the task of guaranteeing your customers rock-solid security for their financial information and online purchases. Consequently, many people turn to dedicated firewall hosting from their hosting provider.
Where Firewall Hosting Comes In
When you’re browsing web hosting plans, you’ll often come across a mention of a firewall. These will protect your website from attacks and malicious traffic.
Something as simple as a flaw in your website code can leave your site vulnerable. Or, perhaps you have weak log-in credentials that can be easily guessed by hackers.

Do Firewalls Protect Against DDoS Attacks?
Firewall protection at the server level can help mitigate the risks associated with these issues. One thing you may have heard of is DDoS protection. Firewalls can help protect your websites from harmful DDoS attacks.
How DDoS Attacks Affect Your Website
A DDoS attack can cause serious downtime for your website. This is the goal of the attack, to make your online service unavailable. This is done by overwhelming your website with traffic from multiple sources.
This is a huge threat to online businesses. In fact, more than 2000 DDoS attacks are observed daily and about a third of all website downtime is caused by DDoS.
Botnets and More
To do this, hackers build up a network of infected computers which are known as botnets. These computers become infected and can be controlled remotely by the hacker. These armies of machines are then used by the hacker to attack a target website, overloading the server and causing an outage.
You don’t want that to happen to your website. This is why most hosting providers make sure to include DDoS protection with their plans. You can usually find this listed in the security features of the hosting plan you’re interested in.
Firewalls Are Not Enough
Firewalls are often the second line of defense from these attacks after DDoS mitigation. This is because firewalls are only designed to prevent one unauthorized access at a time.
They are not designed to detect millions of packets at the same time. Especially since these connections are seen as legitimate because they are coming from computers, as all other website traffic does.
DDoS Mitigation
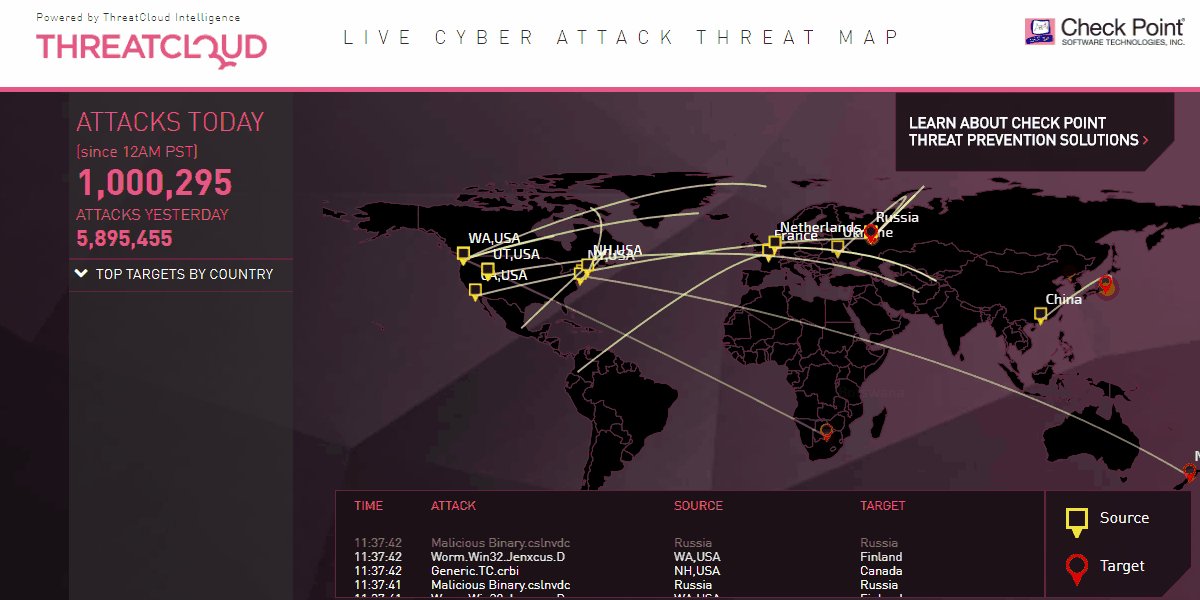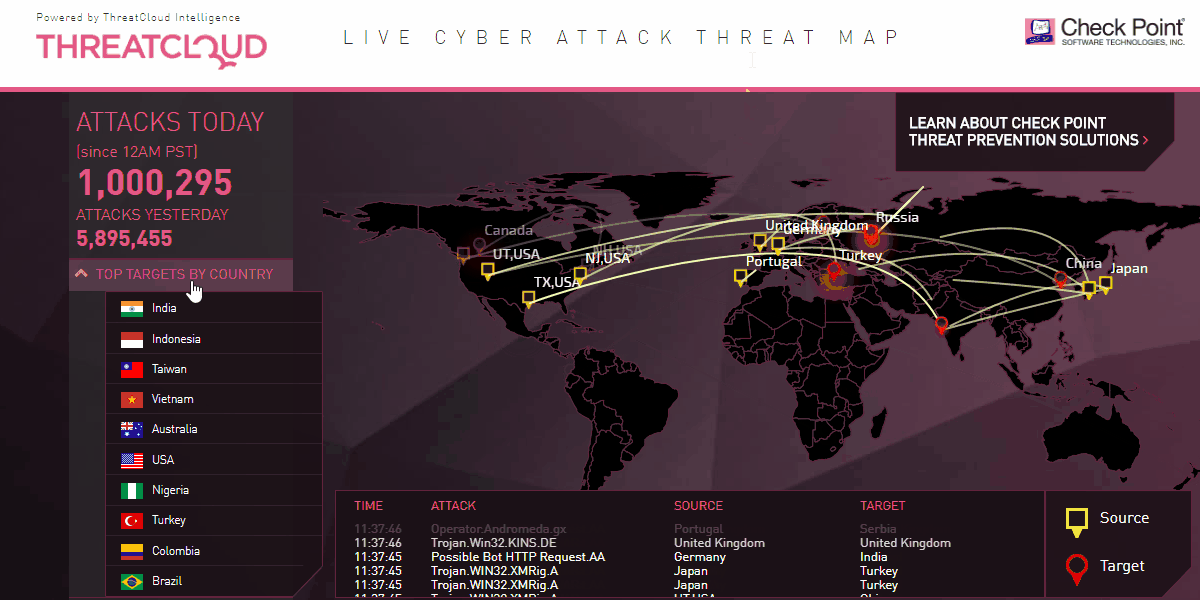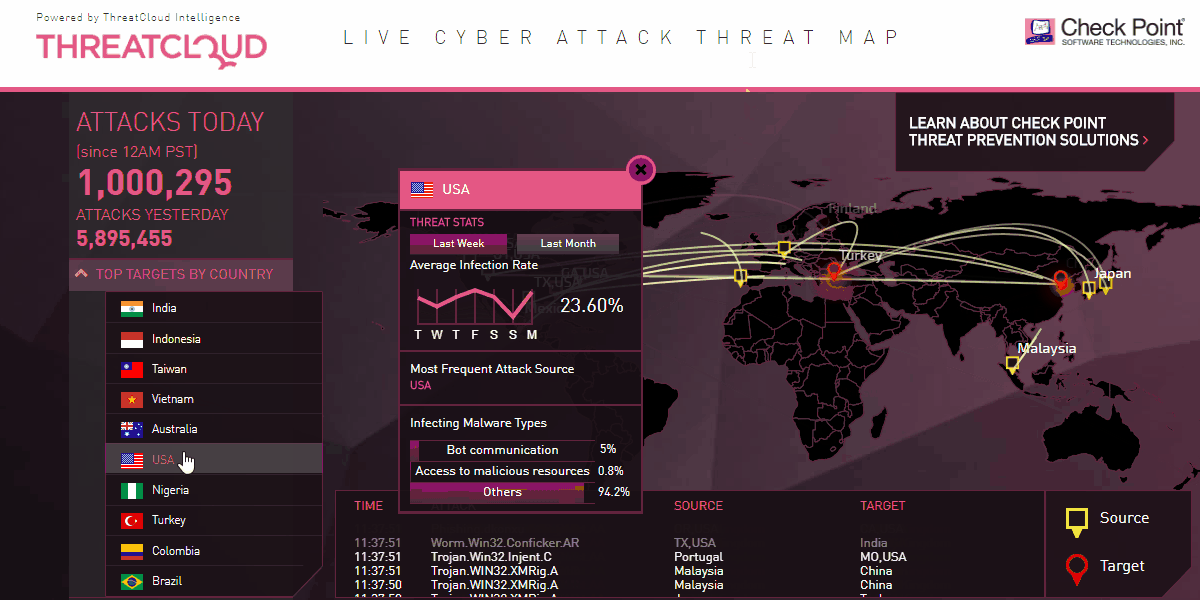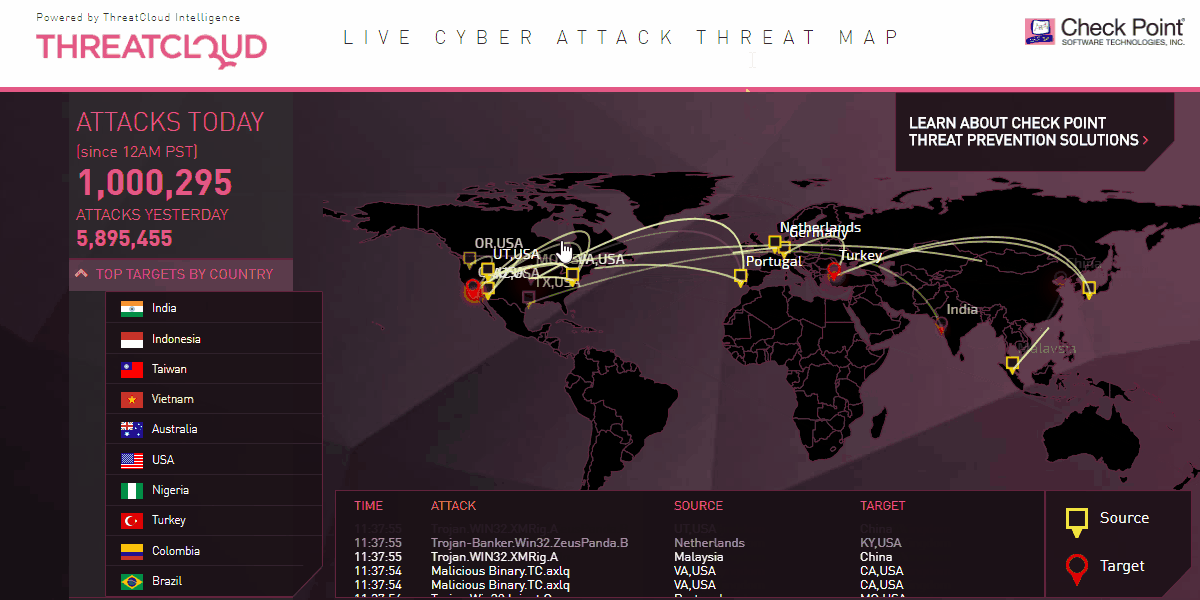
The problem is that a firewall only examines these sessions individually instead of recognizing an unusual flood of them.
DDoS mitigation, on the other hand, is designed to handle millions of connection attempts at the same time. It then recognizes this activity as unusual and blocks the connections.
If your web host just provides a firewall and not DDoS mitigation, you may be more vulnerable to these attacks. Still, firewall protection is better than nothing!
How Firewall Hosting Works
Dedicated firewall hosting boosts your site’s security by providing a combined hardware and software firewall that’s solely for your server (or partition of a shared server, if you use shared hosting or Virtual Private Server (VPS) hosting).
Round-the-clock Monitoring
It often includes round-the-clock monitoring of traffic to and from your site by both the software itself and actual human staffers trained to handle suspicious activity.
Many hosts offer a choice of hardware and software configurations that are scalable based on how much activity your site sees in a given period, and plans are often adjustable “on the fly” to meet sudden surges in traffic to your site.
As a rule, they’ll also include monitoring of specific ports, packet filtering, and protocol filtering.
Packet Filtering
Packet filtering examines each piece of data moving through the system and only lets it through if it meets predefined criteria set by you and your provider.
Port Monitoring and Protocol Filtering
Port monitoring and protocol filtering both involve managing traffic based on the way in which it is trying to interface with your server. Port monitoring masks certain ports (the ‘doors’ through which data travels at various points in the network, including your server, other computers visiting your site, and various network hardware such as routers and switches) or restricts traffic to a specific range of ports.
Traffic Analysis
Protocol filtering, on the other hand, analyzes traffic based on the format it’s using to access the server. Examples include the ubiquitous Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP) and Domain Name Server (DNS, the language used to humanize the numeric information computers use to route traffic on the Internet).
If incoming data seems suspicious or malicious, the software or a technician can stop it in its tracks.
Shared Hosting and Dedicated Servers
One important factor to consider, depending on your level of expertise, is whether the host provides a fully managed firewall, or whether you still maintain a measure of control.
With a fully managed firewall hosting solution, the provider is responsible for managing every aspect of the firewall, including rules, filters, updates, and more. This may be ideal for individuals who lack the expertise or desire to manage the firewall themselves.
For the more advanced user, however, other hosting services allow the end-user to modify the firewall, setting up custom rules or opening and closing ports.
Comparing Shared Hosting vs Dedicated Servers
If your website is on a shared hosting plan, you are sharing the server resources with other customers of your web hosting provider. You may be allocated some specific resources, or it may be a give and take environment between other people on the same server. Either way, you’re sharing the network.
Your host should have a firewall installed, both a hardware firewall and a software firewall. But since you share the same server, you risk other customers having access to your website through the shared firewall.
Though this will provide plenty of protection for individuals and small businesses, larger companies and mission-critical websites may want the added security of a dedicated firewall.
VPS and Firewalls
Of course, shared plans are usually only adequate for smaller businesses anyway. If your business outgrows the shared architecture, this is a good sign that you also need to upgrade your security as well.
VPS and dedicated server plans give website owners much more control and flexibility over their hosting environment. They’re usually very scalable and can handle much larger amounts of traffic than shared environments.
Switching on Your Software Firewall
Along with this, hosting providers should include a built-in hardware firewall into the router. You may have to configure or switch on your software firewall from your control panel in addition to this.
Using cPanel, you’ll only be able to install a software firewall if you have access to Web Host Manager (WHM). This is the back-end administration panel for your server. If you have cPanel on a VPS or dedicated server then you should have WHM access.
To find out if you have firewall software installed, follow these steps:
- Log into WHM from your control panel (use log-in details from your hosting provider)
- Scroll down to the bottom of the page
- Look for a plug-ins tab in the menu
- There should be a firewall plug-in called ConfigServer Security & Firewall (CSF).
- If you don’t see CSF, look for the alternative Firewall software installed
- If you do not have firewall software installed, you can follow installation steps to get it.
Configuring the Software Firewall
Once you have firewall software installed a running, you may want to check some settings on it and configure options. You may want to:
- Check the server security for vulnerable areas and close ports that you don’t need open
- Change the level of firewall security that you need for your website. You should set this to the highest level that still allows your website to function properly
- Install upgrades to the firewall system
- Allow access from your own IP address so the firewall doesn’t mistake you for a security threat
What It Costs
Some hosting providers include a dedicated firewall as part of their hosting packages, but others may charge additional setup or service fees, depending on your level of hosting.
A dedicated firewall can protect your website from hacks and DDoS attacks. It will also help protect your customers’ data when they are using your website. But, the additional cost of dedicated firewalls may be too much for smaller businesses to afford.

Points to Remember
With companies like Target and Home Depot in the news for data breaches, breaches that have exposed the data of millions of customers. There’s no doubt that cybercrime is on the rise.
If you (and your customers) are serious about data integrity and safety, a dedicated firewall just might be worth looking into.
Pros and Cons of Firewall Hosting
Just to remind ourselves, let’s recap what the highlightable upsides are of selecting a host based on firewall availability. In addition, it’s worth keeping loopholes and vulnerabilities in mind too.
Pros:
- Firewalls protect computers from malicious software and corrupt files
- Can help protect your website from DDoS attacks
- Provides network monitoring for suspicious activity
- Prevent unauthorized users from accessing your website
Cons:
- Cannot ensure full protection from DDoS attacks as firewalls were not designed for this
- Dedicated firewalls from hosting companies can be expensive
- Users may be required to manage and configure firewalls themselves which can seem confusing to people who are inexperienced

My Choices – The Best Firewall Protection Hosts
We found several hosts you should check out if you’re looking for firewall protection.
SiteGround
SiteGround for Firewall Protection
SiteGround always comes out on top of our recommended web hosting. Their shared web hosting plans include both a hardware firewall and a local software firewall which includes network traffic monitoring and complex functions.
We love SiteGround because their plans are affordable and their service is amazing. With a variety of options from simple shared hosting, optimized WordPress, cloud hosting, and dedicated servers, SiteGround has something for everyone.
InMotion
InMotion Hosting for Firewall Protection
People hosting with InMotion will also have a pre-installed firewall on their servers. But note that these firewalls are shared and applied to all accounts on the same shared server. Users won’t be able to install a firewall for their own accounts.
People who wish to install their own firewalls will have to use InMotion’s VPS or dedicated server plans. These plans are affordable and include WHM access for managing your server and firewall.
What we love about InMotion hosting is their 99.99% uptime compared to the industry-standard or 99.9%. And, the company has advanced DDoS protection.
LiquidWeb
LiquidWeb for Firewall Protection
LiquidWeb provides hosting for mission-critical websites with their 100% uptime guarantee. Like InMotion and SiteGround, they include an integrated firewall and DDoS protection.
Their VPS plans are fully managed, but users will still have full root access to the servers. With cPanel available, account holders will be able to install their own firewall software on the servers.
You can also add additional firewall protection to your servers through LiquidWeb’s add-ons. These are meant for larger companies as they do not come cheap.

Looking for highly secure hosting?
Liquid Web’s plans feature advanced security and high performance. This host offers DDoS protection, PCI compliance scanning, VPS firewalls, and more. Right now you can get special pricing on their plans by using this discount link.
Firewall Frequently Asked Questions
- Does my site need a firewall?
That’s a decision you’re going to have to make based on the content of your website, how important it is to you that it remains secure, and whether or not you’re receiving sensitive information from your site’s visitors.
If you’re posting a blog about your family vacations, you probably don’t need a firewall. But if you’re hosting an online store or an interactive website that stores user information, you owe it to your users to provide the best security possible.
- Can I make firewall exceptions for others using my site?
Absolutely. In the same way you can tell your desktop’s firewall which programs should be allowed to download information and install updates, you can create exceptions for your server’s firewall.
The degree to which you can customize these rules will depend on your plan, so be sure to do your homework and pick the plan that provides the flexibility you need.
- Do I need a firewall if I’m using SSL encryption?
Encrypting user data is one essential step in securing your customers’ information. However, although encryption systems like SSL allow for the safe transfer of sensitive information over a network, in most cases the actual sensitive information is still being stored on your server, in a format your computer can understand.
In fact, if you are a store owner, you likely have access to much of that sensitive information from your control panel. If you can view that information, so can a hacker who gains access to your server.
- Will I be able to use my VPN with a firewall?
Some hosting companies may provide optional VPN usage. This can be particularly useful for businesses hosting their company’s intranet, as it allows your staff to securely access your server from any location or from their mobile devices.
- Can I get a subset of firewall protection, like just packet filtering and port monitoring?
Your host may provide individual protections, or you may be able to obtain some of them through third party applications. Depending on your needs and the cost savings, this may be a viable option; however, from a total security perspective, any feature you leave out is a potential vulnerability.
Hacking tools are becoming more sophisticated all the time, so a full-service firewall that can adjust to new threats is probably a better approach.
- Are there shared firewall options?
Yes, many hosts will offer (or even provide for free) a shared firewall option. This is typically much less expensive than dedicated firewall protection, but also provides less security and customization.
Since you are sharing the firewall with multiple users, it can only block external requests, not requests made from other computers sharing your firewall, so an attack on one user can be an attack on them all.
- If I opt for the shared firewall, can I upgrade later?
Absolutely. In most cases, changing your firewall preference is simply a matter of adding it through your control panel or giving your host a call.
If you go with the dedicated firewall and then want to downgrade, your host may have rules in place regarding refunds, but the actual process of returning to a shared firewall should be quite simple.
- If I have a firewall in place, does that mean my server is hack proof?
Unfortunately, no. Nothing can guarantee a hack-free online experience.
A single successful hack can earn a data thief enormous sums of money, so there are plenty of hackers willing to dedicate large amounts of their time to getting around the latest security measures.
However, not having a firewall in place makes you much more vulnerable than if you have one, the same way leaving your door wide open makes you an easy target for a burglar.
- What is a Denial-of-Service (DoS) attack?
A DoS attack is an attempt to disrupt or shut down a server, to the effect that traffic is either completely stopped or slowed to a point that most users will be unable to utilize it.
DoS attacks generally involve sending an overwhelming number of communication requests to a server. This leads to the server no longer being able to handle legitimate requests. In some case, this will cause the server to crash.
Regardless, the effect is to make the server unusable for legitimate requests.
- What is a Distributed Denial of Service (DDoS) attack?
A DDoS attack is simply a DoS attack where the attack comes from multiple computers. Very often, such attacks are the result of infected computers that take part in a DDoS attack without knowing it. Today, almost all DoS attacks are distributed.










Comments