

What Is SSH Access?
If you need to frequently access remote systems through unsecured networks, you will most likely want to find a host that supports the Secure Shell (SSH) protocol.
SSH is an encryption protocol for networks created to allow secure connections across unsecured networks and initiate text-based shell sessions on remote machines.
How SSH Encryption Works
It allows the user to run commands on remote computers securely, using a secure channel over an unsecured network. Essentially, this is what it’s all about — the protocol enables a secure channel over an insecure network.
It uses public key cryptography, but manual keys can be employed as well. The protocol relies on one private key and one or more public keys used on the server and client.
You might’ve heard the terms public and private key when talking about Bitcoin.
New to the concepts of encryption and public keys? This video provides a simple and engaging overview.
SSH’s Origins
SSH was developed in 1995 by a Finnish student following a security breach.
Although SSH was originally developed for Linux and other Unix-derived environments, it also operates on other platforms.
When Would You Need to Use SSH?
SSH is commonly used in to log into and communicate with remote machines. In addition to pure shell functionality, SSH also enables users to use:
- Tunneling
- X11 connections
- TCP port forwarding
- Secure file transfers
- Secure copy (SCP) protocols
- SSH file transfer (SFTP) protocols.
SSH is commonly used to log into remote servers, execute server commands or authenticate virtual private network (VPN) users.
Who Can Benefit from SSH?
There are a number of different niches that may benefit from SSH, as it can be used to restrict remote access to servers or to provide users with encrypted, high-security browsing through a proxy connection.
SSH can complement or replace Telnet, rsh, rlogin and other standards in the remote host role. It can also be employed to set up “passwordless” login to remote servers and enable secure file transfers.
How SSH Enhances Security
By using public/private key logins, it is possible to eliminate the need for passwords on remote sites, since attackers will be unable to impersonate you without your private key, which is unfeasible to calculate due to the immense number of possible permutations.
SSH is also becoming increasingly relevant in cloud computing, as it helps address a number of security issues inherent to decentralized cloud platforms.
“Are you serious about network security? Then check out SSH, the Secure Shell, which provides key-based authentication and transparent encryption for your network connections. It’s reliable, robust, and reasonably easy to use, and both free and commercial implementations are widely available for most operating systems.”
– from SSH, The Secure Shell: The Definitive Guide, 2nd Edition by Daniel Barrett, Richard Silverman, Robert Byrnes
SSH: What You Need to Know: Versions, Operating Systems, Ports and More
Here’s a technical quickstart guide to what you need to get up and running with SSH.
SSH Versions: Which One to Use?
The first versions of SSH are now obsolete and cannot provide much security.
Their vulnerabilities were exposed and patched up, resulting in new, more secure versions.
Versions 1.x through 2.x are vulnerable to attack and are no longer in widespread use.
The latest SSH versions are considered secure and SSH-2 is becoming the industry standard.
Which Operating Systems can SSH run on?
While it was originally designed for Linux, SSH is available on most operating systems including:
- Apple’s OS X
- OpenBSD
- FreeBSD
- NetBSD
- Solaris
- OpenVMS
- Most GNU/Linux distributions.
Microsoft platforms do not offer SSH support by default, but support can be added through third-party software.
Which Port Does SSH Use?
TCP port 22 has been assigned for use by SSH servers. In case you are looking to improve security, it is possible to change the default port to non-standard port.
Changing ports involves a bit of tinkering, but also offers additional security through obscurity.
Best Practices with SSH
There is simply no way of making your server 100% secure regardless of what you do, but using the latest SSH standards and tweaked nonstandard configurations should help enhance your security and reduce the number of attack vectors.

Secure Shell Hosting (SSH) Considerations
Since Secure Shell access is quite popular on Linux servers, most hosts tend to offer it and pricing is competitive.
SSH access support may be bundled with various LAMP hosting packages, in which case you can get it for next to nothing, or literally nothing.
SSH Access by Hosting Plan Type
Here’s a quick look at what typical hosting companies provide for SSH access. I’ll go into more detail below the table.
| Hosting Plan Type | SSH Access Availability? |
| Shared | Usually offered by default |
| VPS | Offered by default, including root access |
| Dedicated | Offered by default, including root access |
| Resellers | May require an initial deployment fee |
| Windows Hosting | Needs WinSCP, PuTTY and manual setup for your IP address and SSH port |
SSH and Linux Hosting Plans
Major hosts tend to offer SSH access by default, both on shared and dedicated plans.
Resellers may be required to pay a one-time SSH deployment charge for newly activated accounts.
Dedicated server and VPS customers typically get SSH root access, allowing them more freedom.
SSH and Windows Hosting Plans
As far as Microsoft environments go, the process could be a bit trickier. To use SSH on Windows you need to use WinSCP, PuTTY or a similar solution, then manually set up your IP address and SSH port.
Dozens of SSH clients and servers are available, either as free or commercial services, so you may want to do some research before choosing which one is right for you.
PROTIP: Many developers require Microsoft development tools such as .NET, but at the same time, they need SSH. Although native support is lacking, most hosts offer SSH functionality with their Microsoft packages, so there is nothing to worry about – you should be able to find a plan that meets your requirements with relative ease.
Looking for a great deal on SSH hosting?
InMotion Hosting provides SSH access and excellent technical support on all of its plans. Use this special discount link to save up to 50% on their plans.

How to Use SSH Access
Getting shell access to your host will depend on your hosting account. Not every style of hosting will support SSH access. However, most beginner hosts enable SSH access, unless you’re on a very specialized plan like dedicated WordPress.
Here are the steps you’ll need to take if you want to setup SSH access:
- If you are using an SSH-friendly beginner host, then you’ll need to enable SSH access on your account. Typically this is done through your cPanel.
- Once you’ve enabled SSH you can access your server remotely through an SSH client.
- In order to authenticate your connection, you’ll be using an SSH key.
- You can simply utilize an encrypted password login, but this method isn’t as secure as key authentication.
- With key authentication, you’ll have both a public key and a private key. You need this key pair to validate your connection. The public key can be shared freely, but the private key will be used to verify the connection and must be kept secure.
Established hosting providers like InMotion Hosting typically offer easy-to-follow instructions on how to log into your server using SSH. These instructions may be in video form or available in text via the host’s knowledgebase.
SSH Clients
To access your host remotely via SSH you’ll need an SSH client. There are free clients like Terminal that you might already have installed on your computer.
There is third party software you can use, as well:
| SSH Client | Description | Operating System |
| PuTTY | A popular open-source client that’s similar to Terminal. | Can connect to Unix servers |
| WinSCP | An open-source client for Windows that secures your connection between a local and remote computer. | Windows |
| Fugu | A MacOS graphical interface similar to FTP, but offers encryption. | MacOS |
| Tera Term Pro | An open-source terminal emulator. | For Windows users |
| Bitvise | A fast, lightweight, and secure SSH client. | For Windows users |
Much Programming Experience Do I Need to Utilize SSH Hosting?
The short answer: not any more than you would require accessing your hosting environment through a non-SSH connection.
Secure Shell Hosting (SSH) helps encrypt information sent over two unsecured connections to prevent data breaches while information is in transit.
While you may be required to login via FTP with some specific settings, programming knowledge is not required to connect to a remote server via SSH.
How SSH Can Make Your Life Easier
In order to effectively use SSH, you really won’t need to be any more experienced with programming than you would be if you are using an unsecured connection.
In fact, because SSH uses public and private key logins, the need for remote server passwords may be eliminated altogether.
An SSH connection can actually make things easier for connecting to a remote server when configured correctly.

My Picks for Best SSH Hosting
To help you narrow down your search for a hosting provider, here are the top three hosts I recommend.
InMotion Hosting
If you’re just getting started with SSH hosting, then you might want to consider InMotion.
Currently, SSH access is offered for its shared, dedicated, and VPS hosting packages.

InMotion SSH help page
Not only are its hosting packages competitive, but it’s a very high performing host and has a stellar support team.
If you’re having trouble setting up SSH access, then this support will definitely come in handy.
Bluehost
Bluehost is another solid SSH beginner-friendly host.
Now, SSH access isn’t available straight away, you’ll have to enable SSH on your account.
Luckily, this process is easy an can be enabled from within your cPanel.
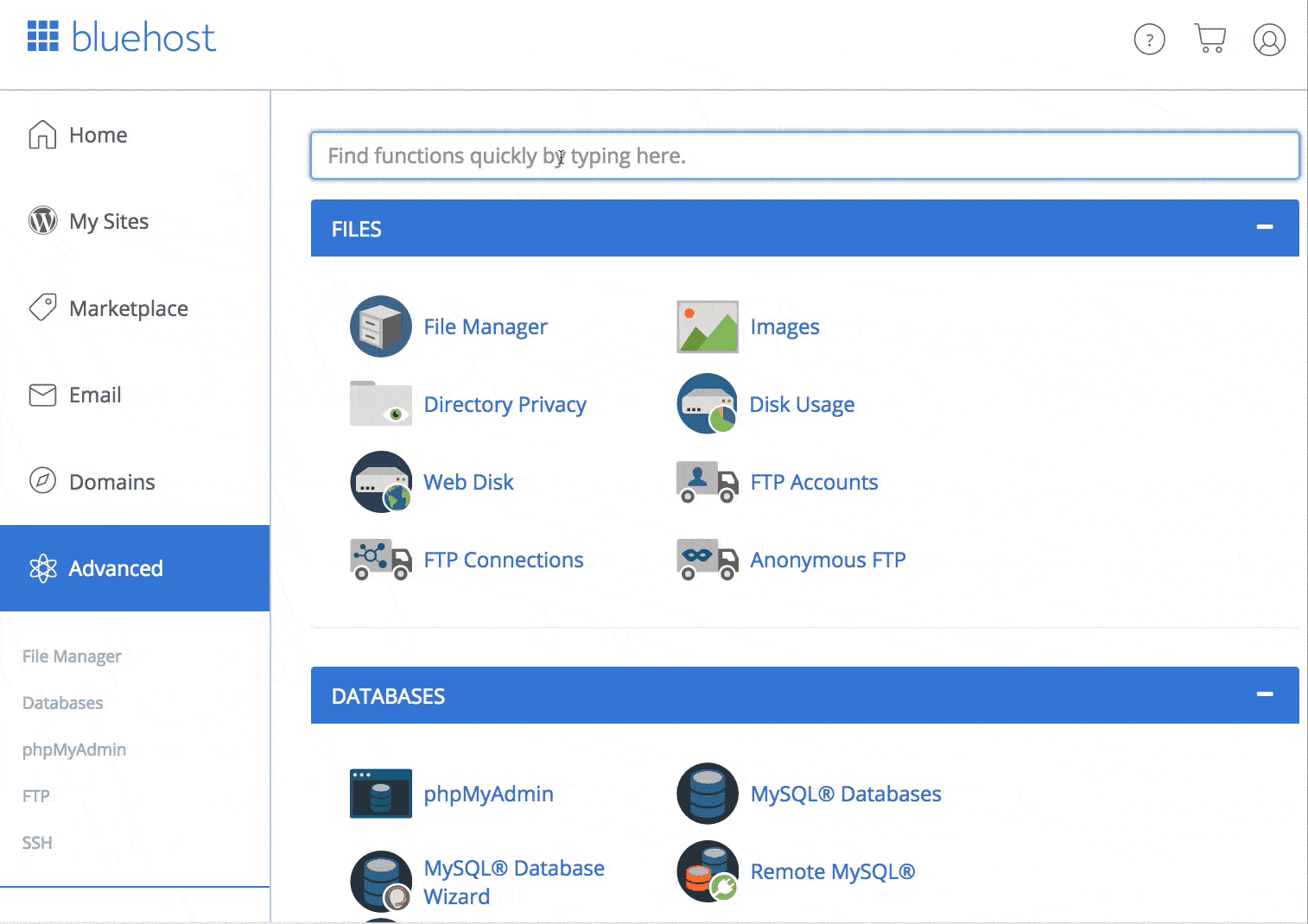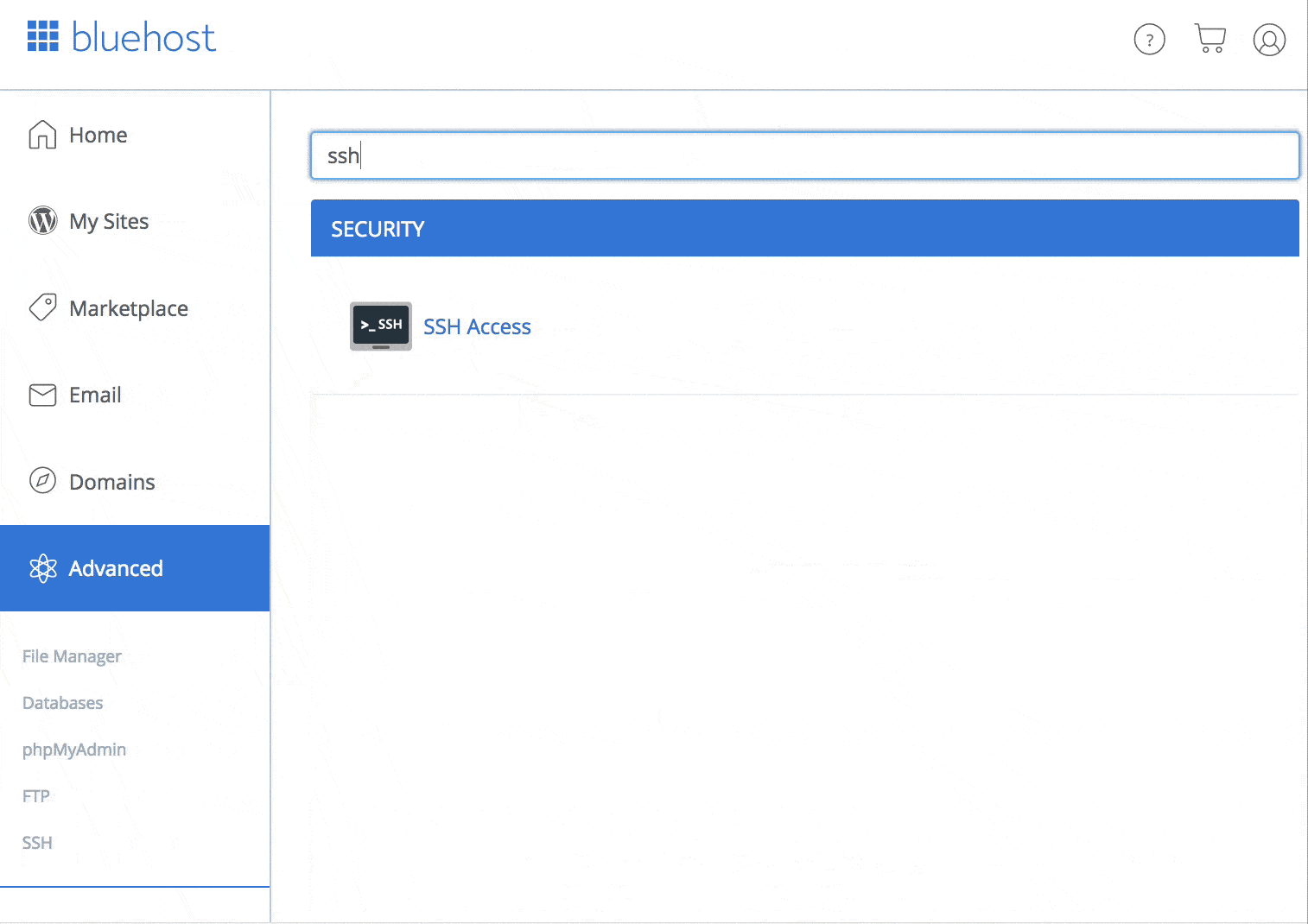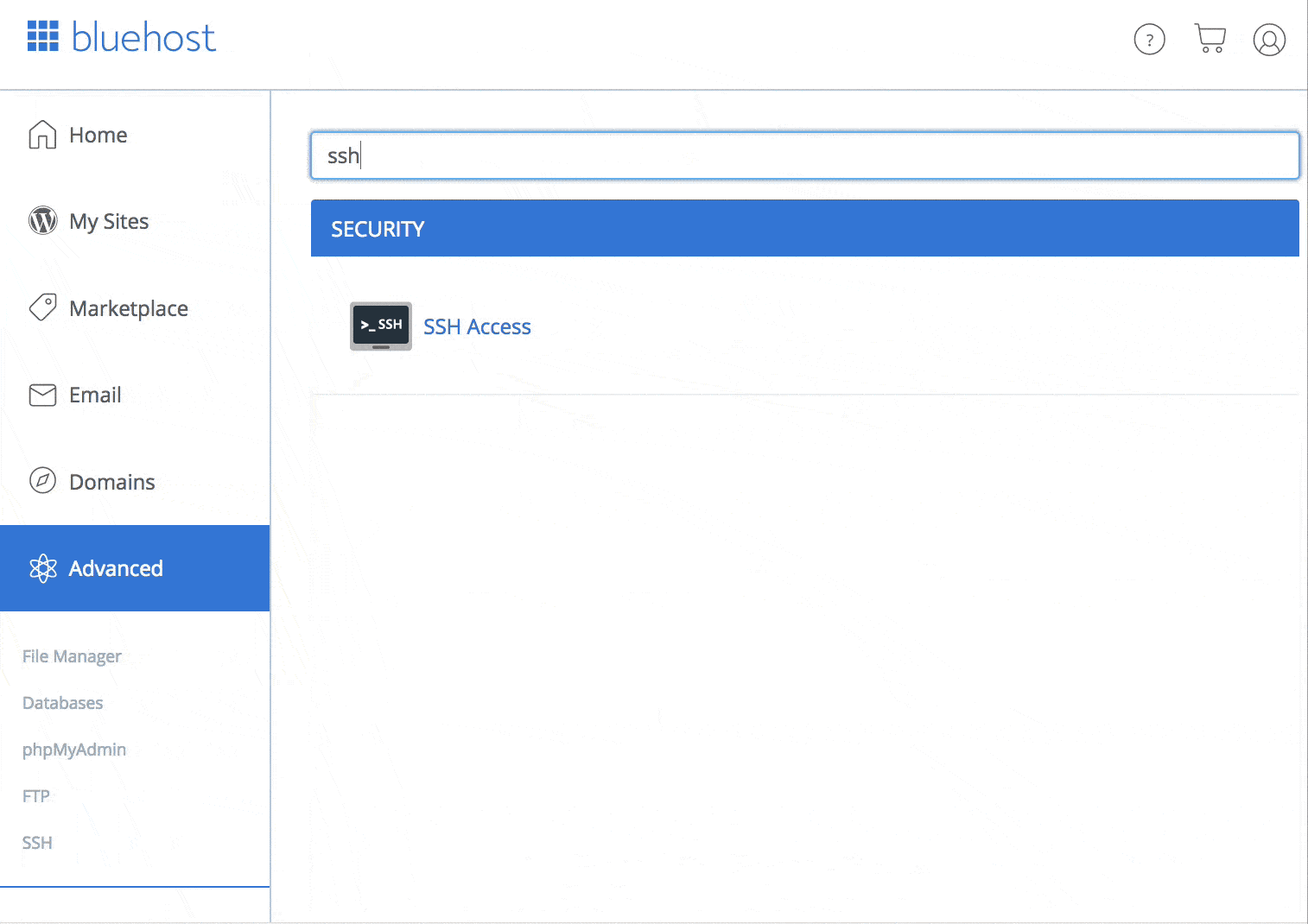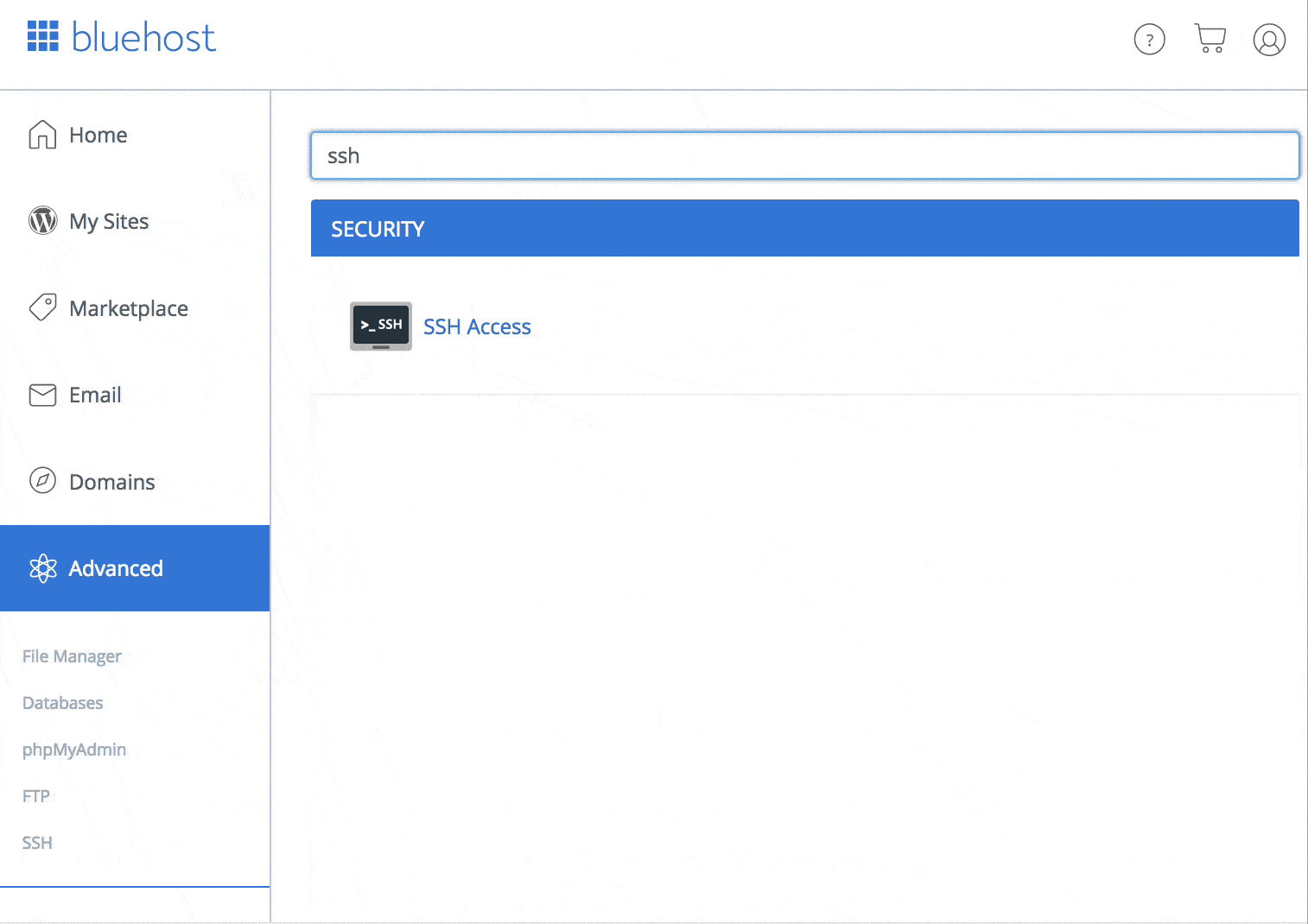
How to find SSH on your Bluehost cPanel
SSH access is available for its shared, dedicated, VPS, and reseller hosting packages.
GreenGeeks
If price isn’t the biggest concern and you don’t mind spending a little more to support the environment, then consider trying GreenGeeks’ hosting plans.

GreenGeeks’ SSH help page
They currently offer SSH access for all of its servers, but instead of configuring it yourself, all you have to do is put in a support request.
This can help to simplify the setup process as the GreenGeeks team will handle the setup for you.
Security Benefits of SSH
SSH uses public-key cryptography to give you a secure way to remotely access your host account. Beyond being able to perform basic tasks like live monitoring your log files, installing software, and even creating MySQL databases, SSH offers you protection against the following:
- DNS spoofing that can divert traffic from its original source
- Data manipulation of networks and routers along access points
- Data transmission snooping or eavesdropping on your connection
- Illegal IP routing that can make your machine think it’s linking to a different destination
- IP address spoofing that makes a malicious computer look safe.
Using SSH Access can Improve Your Website’s Security
Enabling and using SSH access on your hosting plan can improve the security of your website data. It’s not complicated to use but, having said that, it may not be necessary for everyone’s needs.
Still, since it’s usually free, there’s no harm in trying it out to see if you like it.
Other features in Server Administration

Looking for serious hosting with SSH access?
Liquid Web delivers high-performance hosting and superb technical support. Right now you can save up to 50% on their VPS plans. Use this discount link to get the deal.
SSH Access Frequently Asked Questions
- Am I getting the same protection even when using a third-party program?
Yes. The third-party applications available utilize the same protocols as other SSH applications, including the most popular, OpenSSH.
Third-party programs, such as PuTTY, will use a different key file format, but tools are available to translate these to the more common format of OpenSSH if this presents a problem.
- Can SSH be used for file transfers?
Yes. In fact, a number of file transfer protocols have been developed using SSH, including Secure Copy (SCP), rsync, and SSH File Transfer Protocol (SFTP).
- What sort of data can be secured using Secure Shell?
While the primary use for Secure Shell is to log in to remote machines and send commands across computer networks, it can be used to transfer any type of data.
Since it’s a protocol, it can be used to develop any type of application or even another protocol.
For example, SSH File Transfer Protocol was built upon FTP to provide a much higher level of security when uploading and downloading files from a server.
- Do all browsers support Secure Shell?
All modern browsers support Secure Shell. SSH is used by millions of websites across the world and has become a standard security feature.
Unless you’re running an early version of Netscape Navigator, you should have no problem accessing sites that utilize SSH.
- Is SSH an open-source protocol?
The protocol itself is. The SSH-2 protocol is open-source.
However, the implementations of SSH-2 vary. The version of SSH provide by SSH Communications Security contains proprietary components, so much of it is not open source.
Several open-source versions of SSH exist, the best known being OpenSSH.
- Are open-source SSH client less secure?
No. The code is not what provides the security. The use of the public and private keys provide the security. Having access to the source code for a Secure Shell client will not provide data thieves with the ability to interpret your private key.
- Are there other public key encryption protocols available?
There are a number of other public key encryption protocols, some of which provide alternatives to SSH.
One of the most popular public key encryption protocols is Secure Socket Layer (SSL), which is widely used to secure data and verify authenticity over computer networks. SSL is best known for providing secure web traffic, which can be verified by the lock image in your browser’s address bar.
Pretty Good Privacy (PGP) is commonly used to sign, encrypt, and decrypt information contained in email communications. Other examples include S/MIME, ZRTP, SILC, and even bitcoin.
- Where can I get support for SSH?
Support is typically provided specific to the implementation you’re using. For instance, OpenSSH provides a number of FAQs and manuals, in addition to community support via a mailing list.
SSH Communications Security provides several levels of technical support, most for a fee. Your first stop should be your host. Find out if they have support available and check what implementation they’re providing.
- Is Secure Shell available on mobile platforms?
Yes. A number of programs exist to bring SSH protocols to mobile devices, including pTerm for iOS and ConnectBot for Android.
However, if you just want to access an SSH-secured server using your mobile phone, you don’t need to worry about applications like this. Your browser should have no problem communicating with the SSH server.
- How do I install an SSH client?
One is probably already provided through your hosting plan. If not, or if you want to utilize a different SSH client, you can usually download a copy from their website.
If you decide to install SSH manually, be sure to check with your host to make sure it is compatible.










Comments