
Infographic: Nine Tips for Keeping Your Internet Usage Private

Disclosure: Your support helps keep the site running! We earn a referral fee for some of the services we recommend on this page. Learn more

The loss of privacy in the golden age of the Internet has quickly gone from troubling possibility to uncomfortable reality. Ours is a world immersed in information, and oversharing has become the rule, rather than the exception.
Every single minute, 639,800 gigabytes of information is transmitted around the ‘Net: 47,000 apps are downloaded, Google handles more than two million searches, and 100,000 bon mots, adverts, and assorted logorrhea appear on Twitter in the form of tweets. The information superhighway’s expanding exponentially, and new batches of data are ready to go tearing down the lanes as soon as they’re laid.
Of course, not all this sharing is funny cat videos or hipster-fied pics of your niece’s lunch. In that same “Internet minute,” twenty people find they’ve become the victims of identity theft. Countless more, however, are victims of a far more insidious sort of theft: data mining.
Depending on the browser and services you use, your every click, website review, and online purchase can be collected, analyzed and used to create a profile that’s readily sold off to advertisers and government agencies. A quick visit to a gardening website could mean ads for heirloom tomato seeds are in your Facebook future; buying a bingo bag for your sweet old aunt Mildred could lead to unlooked-for AARP adverts in your mailbox.
And that’s just the tip of the information iceberg. The same profile that notes your love of ’80s rock and romantic movies often also contains less frivolous information such as your home address, phone number, and even your social security number. If you’re looking to set up a website and you also register a domain, your personal info is readily visible in Whois search results unless you pay to protect it.
Fortunately, you can take steps to protect your privacy, even in an age of “free” apps and crazily-specific targeted ads. Encrypting your files, emails, and domain information (if desired) is a good start. Switching to a more secure browser, and—if you have the emotional wherewithal—even pulling the social media plug altogether are just some of the other ways you can keep your personal information from becoming a public matter.
PS. You can now also download this infographic in Dutch and Spanish c/o our friends at DynamoSpanish.com.
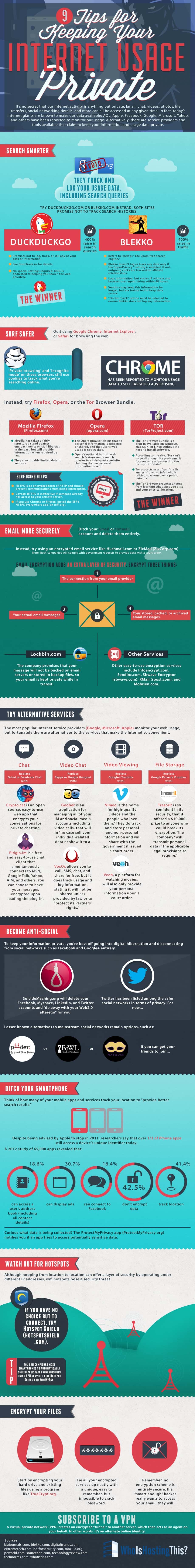
9 Tips for Keeping Your Internet Usage As Private As Possible
It’s no secret that our Internet activity is anything but private. Email, chat, videos, photos, file transfers, social networking details, and more can all be accessed at any given time. In fact, today’s Internet giants are known to make our data available: AOL, Apple, Facebook, Google, Microsoft, Yahoo, and others have been reported to monitor our usage. Alternatively, there are service providers and tools available that claim to keep your information and usage data private.
Search Smarter
Avoid using Microsoft Bing and Google, as they track and log your usage data, including search queries.
Try DuckDuckGo.com or Blekko.com instead. Both sites promise not to track search histories.
- In the first half of 2012, Blekko saw a nearly 400% gain in unique visitors.
- DuckDuckGo’s queries increased by almost 400%, averaging nearly 1.5 million queries/day in 2012.
Blekko vs. DuckDuckGo
DuckDuckGo:
- Promises not to log, track, or sell any of your data or information.
- See us for details.
Blekko:
- Refers to itself as “The spam-free search engine.”
- Blekko doesn’t log or track any data only if the SuperPrivacy™ setting is enabled. If not, outgoing clicks are tracked for affiliate relationships.
- Logs information, but erases IP address and browser user agent string within 48 hours.
- Vendors may keep this information for longer, but are instructed to keep data secure.
- “Do Not Track” option must be selected to ensure Blekko does not log any information.
The Winner: DuckDuckGo
No special settings required, DDG is dedicated to helping you search the web privately.
Surf Safer
Do Not Track Settings
- DNT settings in web browsers send tracking preferences to websites, indicating you do not want to be tracked for behavioral marketing.
- DuckDuckGo claims these settings are ineffective because they’re completely voluntary as determined by the visited websites. They simply limit the number of targeted ads a visitor sees.
Quit using Google Chrome, Internet Explorer, or Safari for browsing the web.
‘Private browsing’ and ‘incognito mode’ on these browsers still use cookies to track what you’re searching online.
Chrome has been reported to monitor usage data to sell targeted advertising.
Instead, try Firefox, Opera, or the Tor Browser Bundle.
Firefox vs. Opera vs. Tor
Mozilla Firefox (Firefox.com)
- Mozilla has taken a fairly structured stand against encroachments on civil liberties in the past, but will provide information when required by law.
- They also provide limited data to vendors.
Opera (opera.com)
- The Opera Browser claims that no personal information is collected or shared, and that user’s web usage is not tracked.
- Opera’s optional built-in web search feature sends search queries to a third-party website, claiming that no personal information is sent.
Tor (TorProject.com)
- The Tor Browser Bundle is a plug-in available on Windows, Mac OS X, or Linux without the need to install software.
- According to the site, “Tor can’t solve all anonymity problems. It focuses only on protecting the transport of data.”
- Tor protects users from “traffic analysis” used to infer who is talking to whom over a public network.
- The Tor Browser prevents anyone from learning what sites you visit and your physical location.
The Winner: Tor
Surf using HTTPS
- HTTPS is an encrypted form of HTTP and should prevent communications from being intercepted.
- Caveat: HTTPS is ineffective if someone already has access to your remote server.
- If you use Chrome or Firefox, install the EFF’s HTTPS Everywhere add-on (eff.org).
Email More Securely
Ditch your Gmail or Hotmail account and delete them entirely.
Instead, try using an encrypted email service like Hushmail.com or ZixMail (ZixCorp.com).
Note: Both companies will comply with government requests to provide data with a court order.
Email encryption adds an extra layer of security. Encrypt three things:
- The connection from your email provider;
- Your actual email messages; and
- Your stored, cached, or archived email messages.
Another option is Lockbin.com, a free web app for sending private, encrypted email messages & files.
The company promises that your message will not be backed on email servers or stored in backup files, so your email is kept private while in transit.
Other easy-to-use encryption services include Infoencrypt.com, Sendinc.com, Sbwave Encryptor (sbwave.com), RMail (rpost.com), and Mobrien.com.
Plugin services for encryption like Mailvelope.com or SafeGmail are also worth checking out.
Although they may prevent interception of messages in transit, they also have setbacks:
- With SafeGmail, you cannot choose when your email is deleted, and the built-in system can take days.
- Attachments are not encrypted.
- In order for the recipient to see a message, they must copy and paste the code into a separate window.
- Mailvelope stores the keys in the local storage of the browser.
Try Alternative Services
The most popular Internet service providers (Google, Microsoft, and Apple) monitor your web usage, but that doesn’t mean there’s not alternatives to the services that make the Internet so convenient.
Chat: Try Crypto.cat or Pidgin.im instead of Gchat or Facebook Chat.
- Crypto.cat is an open source, easy-to-use web app that encrypts your conversations for private chatting.
- Pidgin.im is a free and easy-to-use chat client that simultaniously connects to MSN, Google Talk, Yahoo, AIM, and others. You can choose to have your messages encrypted upon loading the plug-in.
Video chat: With both Skype and Google Hangouts tracking our usage and loging our information, try goober.com or VoxOx.com, but we suggest goober.
- Goober is an application for managing all of your IM and social media accounts including video calls, that will in “no case sell your individual-related data or show it to a third person for any reason.”
- VoxOx allows you to call, SMS, chat, and share for free, but it does track usage and log information, stating it will not be shared unless provided by law or to “protect its Partners’ rights.”
Video viewing: Rather than Google’s YouTube, check out Vimeo.com, Veoh.com, or Dailymotion.com.
- Vimeo is “the home for high-quality videos and the people who love them.” They do track and store personal and non-personal information and will share with the government if issued a court order.
- Veoh, a platform for watching movies, will also only provide your personal information upon a court order.
- Dailymotion, a French company, is the only video site listed that doesn’t provide data to third parties, but they will provide personal info in accordance with the law.
File storage, syncing & sharing: Try Tresorit.com in place of Google Drive or Dropbox.
- Tresorit is so confident in its security, that it offered a $10,000 prize to anyone who could break its encryption. The company “will transmit personal data if the applicable legal provisions so require.”
Become Anti-Social
To keep your information private, you’re best off going into digital hibernation and disconnecting from social networks such as Facebook and Google+ entirely.
SuicideMaching.org will delete your Facebook, Myspace, LinkedIn, and Twitter accounts and “do away with your Web2.0 alterego” for you.
Twitter has been listed among the safer social networks in terms of privacy. For now…
Lesser-known alternatives to mainstream social networks remain options, such as:
- Pidder.com
- Friends of Wikileaks
- and p2p social network, Masque (www.findmasques.org)
…if you can get your friends to join.
Ditch Your Smartphone
Think of how many of your mobile apps and services track your location to “provide better search results.”
Despite being advised by Apple to stop in 2011, researchers say that over 1/3 of iPhone apps still access a device’s unique identifier today.
A 2012 study of 65,000 apps revealed that:
- 18.6%can access a user’s address book (including all contact details)
- 30.7% can display ads
- 16.4% can connect to Facebook
- 42.5% don’t encrypt data
- 41.4% track location
Curious what data is being collected? The ProtectMyPrivacy app (ProtectMyPrivacy.org) notifies you if an app tries to access potentially sensitive data.
Watch Out For Hotspots
Although hopping from location to location can offer a layer of security by operating under different IP addresses, Wi-Fi hotspots pose a security threat.
If you have no choice but to connect, try Hotspot Shield (hotspotshield.com).
You can configure most smartphones to automatically shield your data from hotspots using VPN services like Hotspot Shield and HideMyAss.
Encrypt Your Files
Start by encrypting your hard drive and existing files using a program like TrueCrypt.org.
Tie all your encrypted services up neatly with a unique, easy to remember, but impossible to crack password.
Remember, no encryption scheme is entirely secure. If a “smart enough” hacker really wants to access your email, they will.
Subscribe to a VPN
A virtual private network (VPN) creates an encrypted “tunnel” to another server, which then acts as an agent on your behalf. In other words, it’s an alternate online identity.
Check out services like iVPN or Hidemyass.
Sources
- Tired of Obama Reading Your Emails? Try These Services to Protect Yourself from PRISM – bizjournals.com
- How to Use the Internet Without All Those Prism-Accused Web Properties – digitaltrends.com
- How NSA’s Prism Affects You, and How to Protect Yourself from Being Spied On – extremetech.com
- How to Protect Your PC from Prism Surveillance – pcworld.com
- Best Free Software for Protecting Your PC and Your Privacy – pcworld.com
- blog.blekko.com
- blekko.com
- Don’t Track Us – whatisdnt.com
- Mozilla Privacy Policy – mozilla.org
- Safe Gmail Lets You Send Private Encrypted Emails in Chrome – technorms.com
- Study Shows Many iPhone Apps Defy Apple’s Privacy Advice – technologyreview.com



Infographic: Nine Tips To Keep Your Internet Usage Private | Unix Samurai
October 16, 2015
[…] The infographic above is from WhoIsHostingThis.com […]