
How to Stay Anonymous Online in 2014

Disclosure: Your support helps keep the site running! We earn a referral fee for some of the services we recommend on this page. Learn more

Internet privacy has been all over the news lately, with the NSA in the spotlight for overstepping its bounds in surveillance. For decades, they’ve been infecting computers with monitoring software to track citizens and compile data on their every click.
And it’s not just criminals and terrorists that are being monitored: 90% of the people the NSA watches aren’t suspected of any crime.
Citizens of the US and other countries being censored and monitored feel that we’re sacrificing our personal privacy, internet openness, and freedom of expression, in the name of dubious increased security. Research shows that this overzealous surveillance costs us not only in personal privacy, but in economic costs, and is eroding people’s trust in their own government. Internet trust, recent surveys show, is at an all-time low.
It’s a common defense that those who have nothing to hide have nothing to worry about. But the “nothing to hide” fallacy hurts us all as a society. With thousands of laws on the books, any one of us could be accused of some obscure wrongdoing. And when the government can prosecute anyone and everyone, they can pick and choose who they put away, according to their whims or the highest bidder.
People around the world want the freedom to gain knowledge and express themselves without ending up on a government watchlist. When citizens live their daily lives in fear of prosecution, when we fear being able to dissent against our own government, we’re not truly free.
Even if you do have nothing to hide, you have a right to keep your personal information private. Are you 100% comfortable with any NSA employee being able to access your personal data and internet history on a whim?
And when we don’t know what the government is watching, what data they’re collecting, and what they’re doing with that data, how do we know for certain we have nothing to fear?
Today, your every action online could be monitored and recorded. However, there are several options for maintaining anonymity and evading surveillance online.
While it may be impossible to keep your data 100% safe, the options outlined below will give you some measure of protection against surveillance.
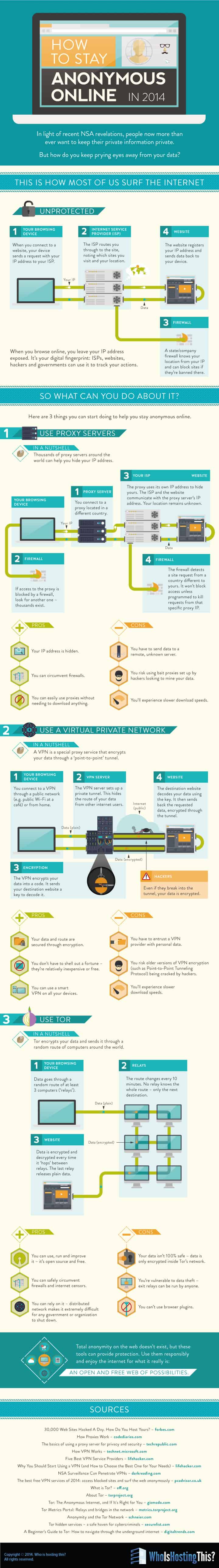
How to Stay Anonymous Online in 2014
In light of recent NSA revelations, people now more than ever want to keep their private information private.
But how do you keep prying eyes away from your data?
This Is How Most of Us Surf the Internet:
Unprotected
- Your Browsing Device
- When you connect to a website, your device sends a request with your IP address to your ISP.
- Internet Service Provider (ISP)
- The ISP routes you through to the site, noting which sites you visit and your location.
- Firewall
- A state/company firewall knows your location from your IP and can block sites if they’re banned there.
- Website
- The website registers your IP address and sends data back to your device.
When you browse online, you leave your IP address exposed. It’s your digital fingerprint: ISPs, websites, hackers and governments can use it to track your actions.
So what can you do about it?
Here are 3 things you can start doing to help you stay anonymous online.
- Use Proxy Servers
- In a nutshell: Thousands of proxy servers around the world can help you hide your IP address.
- Proxy Server
- You connect to a proxy located in a different country.
- Your Browsing Device
- Firewall
- If access to the proxy is blocked by a firewall, look for another one &ndash thousands exist.
- Your ISP, the Website
- The proxy uses its own IP address to hide yours. The ISP and the website communicate with the proxy server’s IP address. Your location remains unknown.
- Firewall
- The firewall detects a site request from a country different to yours. It won’t block access unless programmed to kill requests from that specific proxy IP.
Pros:
- Your IP address is hidden.
- You can circumvent firewalls.
- You can easily use proxies without needing to download anything.
Cons:
- You have to send data to a remote, unknown server.
- You risk using bait proxies set up by hackers looking to mine your data. You’ll experience slower download speeds.
- Use a Virtual Private Network
- In a nutshell: A VPN is a special proxy service that encrypts your data through a ‘point-to-point’ tunnel.
- Your Browsing Device
- You connect to a VPN through a public network (e.g. public Wi-Fi at a café) or from home.
- VPN Server
- The VPN server sets up a private tunnel. This hides the route of your data from other internet users.
- Encryption
- The VPN encrypts your data into a code. It sends your destination website a key to decode it.
- Hackers
- Even if they break into the data tunnel, your data is encrypted.
- Website
- The destination website decodes your data using the key. It then sends back the requested data, encrypted through the tunnel.
Pros:
- Your data and route are secured through encryption.
- You don’t have to shell out a fortune – they’re relatively inexpensive or free.
- You can use a smart VPN on all your devices.
Cons:
- You have to entrust a VPN provider with personal data.
- You risk older versions of VPN encryption (such as Point-to-Point Tunneling Protocol) being cracked by hackers.
- You’ll experience slower download speeds.
- Use Tor
- In a nutshell: Tor encrypts your data and sends it through a random route of computers around the world.
- Your Browsing Device
- Data goes through a random route of at least 3 computers (‘relays’).
- Relays
- The route changes every 10 minutes. No relay knows the whole route – only the next destination.
- Website
- Data is encrypted and decrypted every time it ‘hops’ between relays. The last relay releases plain data.
Pros:
- You can use, run and improve it – it’s open source and free.
- You can safely circumvent firewalls and internet censors.
- You can rely on it – distributed network makes it extremely difficult for any government or organization to shut down.
Cons:
- Your data isn’t 100% safe – data is only encrypted inside Tor’s network.
- You’re vulnerable to data theft – exit relays can be run by anyone.
- You can’t use browser plugins.
Total anonymity on the web doesn’t exist, but these tools can provide protection. Use them responsibly and enjoy the internet for what it really is: an open and free web of possibilities.
Sources
- The Basics of Using a Proxy Server for Privacy and Security – techrepublic.com
- How VPN Works – technet.microsoft.com
- Five Best VPN Service Providers – lifehacker.com
- What is Tor? – eff.org
- The Best Free VPN Services of 2015 for UK Users: Access Blocked Sites and Surf the Web Anonymously – pcadvisor.co.uk
- Tor: Overview – torproject.org
- Anonymity and the Tor Network – schneier.com
- Tor Hidden Services – a Safe Haven for Cybercriminals – securelist.com
- A Beginner’s Guide to Tor: How to Navigate through the Underground Internet – digitaltrends.com
- How Proxies Work – codediaries.com
- Why You Should Start Using a VPN (and How to Choose the Best One for Your Needs) – lifehacker.com
- NSA Surveillance Can Penetrate VPNs – darkreading.com
- Tor: The Anonymous Internet, and If It’s Right for You – gizmodo.com
- Tor Metrics – Servers – metrics.torproject.org




Comments