
How To Use Tor For Private Web Browsing

Disclosure: Your support helps keep the site running! We earn a referral fee for some of the services we recommend on this page. Learn more

With all the news about NSA and other government organizations around the world, it seems like everything we do, whether physical or virtual, is being watched by somebody. We now know that our phone calls, texts, emails, and online activities are all being recorded and monitored, and who knows what else?
Some may say that if you have nothing to hide, you have nothing to fear. Surely only criminals should fear getting caught if the government is spying on all of us, right?
But there’s an argument to be made that when a government constantly watches everything its citizens do, it harms society as a whole.
Criminals aren’t the only people who desire privacy. The United Nations recognizes privacy as a fundamental human right, and many countries protect their citizens’ privacy rights explicitly in their constitutions. As the ACLU says, “Privacy is a fundamental part of a dignified life.” It enables freedom of expression and individual autonomy without fear of reprisal.
The “nothing to hide” argument also goes against the principle of “innocent until proven guilty,” a principle which the justice systems of many countries in the world follow. Instead, constant government surveillance of its citizens assumes that all of them are criminals who have something to hide.
Add to all that the fact that we don’t even know for sure why they’re watching us, and what they’re doing with all our data, and we have even more reasons to be suspicious of the constant surveillance.
What can we do besides signing ineffective petitions on sites like Change.org and sharing the gloomy news with our Facebook friends? It seems like all the protests are simply ignored by governments, who tell us their spying is for our own good.
But there is something you can do to protect your information while browsing online, and it doesn’t require you to be an IT expert or technical genius. Using the TOR browser, you can remain anonymous online and protect your right to privacy. Here’s how to get started.
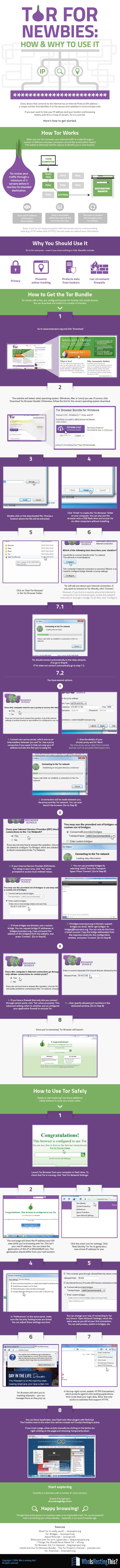
A Newbie’s Guide to Tor: How to Get It, Use It and Why
Every device that connects to the internet has an Internet Protocol (IP) address – a unique number that identifies it to the servers and websites it communicates with.
If you ever want to hide your IP address (and your location and browsing history with it) in a maze of servers, Tor is a sure bet.
Here’s how to get started.
How Tor Works
When you use Tor’s browser, your internet traffic is routed through a number of different volunteer computers around the world (called ‘relays’). This makes it extremely hard for anyone to identify you or your location.
Why You Should Use It
Tor is for everyone – even if you have nothing to hide. Benefits include:
- Privacy
- Prevents online tracking
- Protects data from hackers
- Can circumvent firewalls
How to Get the Tor Bundle
Tor comes with a free, pre-configured browser for desktop and mobile devices. You can download and install it in a matter of minutes:
- Go to torproject.org and click ‘Download’.
- The website will detect what operating system (Windows, Mac or Linux) you use. If correct, click ‘Download Tor Browser Bundle’. Otherwise, follow the link for the correct operating system download.
- Double-click on the downloaded file. Choose a location where the file will be extracted.
- Click ‘Finish’ to create the ‘Tor Browser’ folder on your computer. You can also put the browser onto a USB flash drive and access Tor on other computers without installing.
- Click on ‘Start Tor Browser’ in the Tor Browser folder.
- Tor will ask you about your internet connection. If you want to connect to Tor directly, click ‘Connect’.
However, if you live in a country where the internet is censored or Tor is frowned upon, access the network indirectly or through a ‘bridge’. To do this, click ‘Configure’.
- Tor will connect automatically to the relay network. If so, go to Step 8. If Tor does not connect automatically go to step 7.1.
You have several options.
- 7.1.A. Connect via a proxy server, which acts as an intermediary between you and Tor. Use a proxy connection if you want to hide not only your IP address but also the fact you’re using Tor.
- 7.1.B. Give the details of your chosen proxy and hit ‘Next’.
Tip: Use proxy server data from trusted sources such as proxylist.hidemyass.com.
- 7.1.C. A connection will be made between you, the proxy and the Tor network. You can now launch the browser. Go to Step 8.
- 7.2.A. If your Internet Service Provider (ISP) blocks Tor relays in your area, click ‘Yes’ when prompted to access local unlisted relays.
- 7.2.B. You can use provided bridges by selecting ‘obfs3’ from the Transport types. Press ‘Connect’.
- 7.2.C. If those bridges are blocked, use a custom bridge. You can request bridge IP addresses at bridges.torproject.org. Copy and paste the address of the bridge(s) from the website, and press ‘Connect’.
- 7.2.D. If bridges.torproject.org is blocked, request bridges via email. Write ‘get bridges’ to [email protected]. You can only do this from a Gmail account. Copy the bridge address(es) from the response email into the configuration window, and press ‘Connect’.
- 7.3.A. If you have a firewall that only lets you connect through certain ports, click ‘Yes’ when prompted. This advanced setting refers to whether you’ve configured your application firewall to exclude Tor.
- 7.3.B. …then specify allowed port numbers in the dedicated window.
- Once you’re connected, Tor Browser will launch.
How to Use Tor Safely
Ready to start exploring? Use these additional safety features to cover your tracks online.
- Launch Tor Browser from your computer or flash drive. To check that Tor is running, click ‘Check Tor Network Settings’.
- The next page will show the IP address your ISP sees while you’re browsing with Tor. This isn’t your real IP address. You can check the geolocation of this IP at whatismyipaddress.com. The geolocation should differ from your real location.
- Click the onion icon for settings. Click ‘New Identity’ for Tor to generate a new virtual IP address for you.
- In ‘Preferences’ on the same panel, make sure the Security Setting boxes are ticked. You can adjust these settings any time.
- You can change your way of connecting to Tor any time in ‘Open Network Settings’, much the same way as you did at your first connection. You can add proxies, switch to bridges, etc.
- Tor Browser will alert you to tracking attempts – you can manage these as they pop up.
- In the top-right corner, enable ‘HTTPS Everywhere’, which protects against click-jacking applications that could steal your login data. Note: this only works on websites that support HTTPS.
- You can block JavaScripts, Java Flash and other plugins with NoScript. The S button next to the onion icon will be crossed out if script blocking is active.
If you trust a page, allow scripts manually by clicking on the button (or right-clicking on the page) and choosing ‘temporarily allow’.
Happy browsing!
Though total online privacy is nowadays seen as an impossible myth, Tor can be powerful tool in protecting your online identity – especially in our post-Snowden age.
Sources
- Want Tor to really work? – torproject.org
- Tor: Bridges – torproject.org
- About NoScript – noscript.net
- Bittorrent over Tor isn’t a good idea – blog.torproject.org
- 7 Things You Should Know About Tor – eff.org
- Tor Browser 3.6.2 is released –blog.toproject.org
- Install and Use Tor Browser Bundle – The Tor Project’s Channel – youtube.com
- Tor: Overview –torproject.org




Comments