Can a simple lookup decide whether a site loads in seconds or never appears?
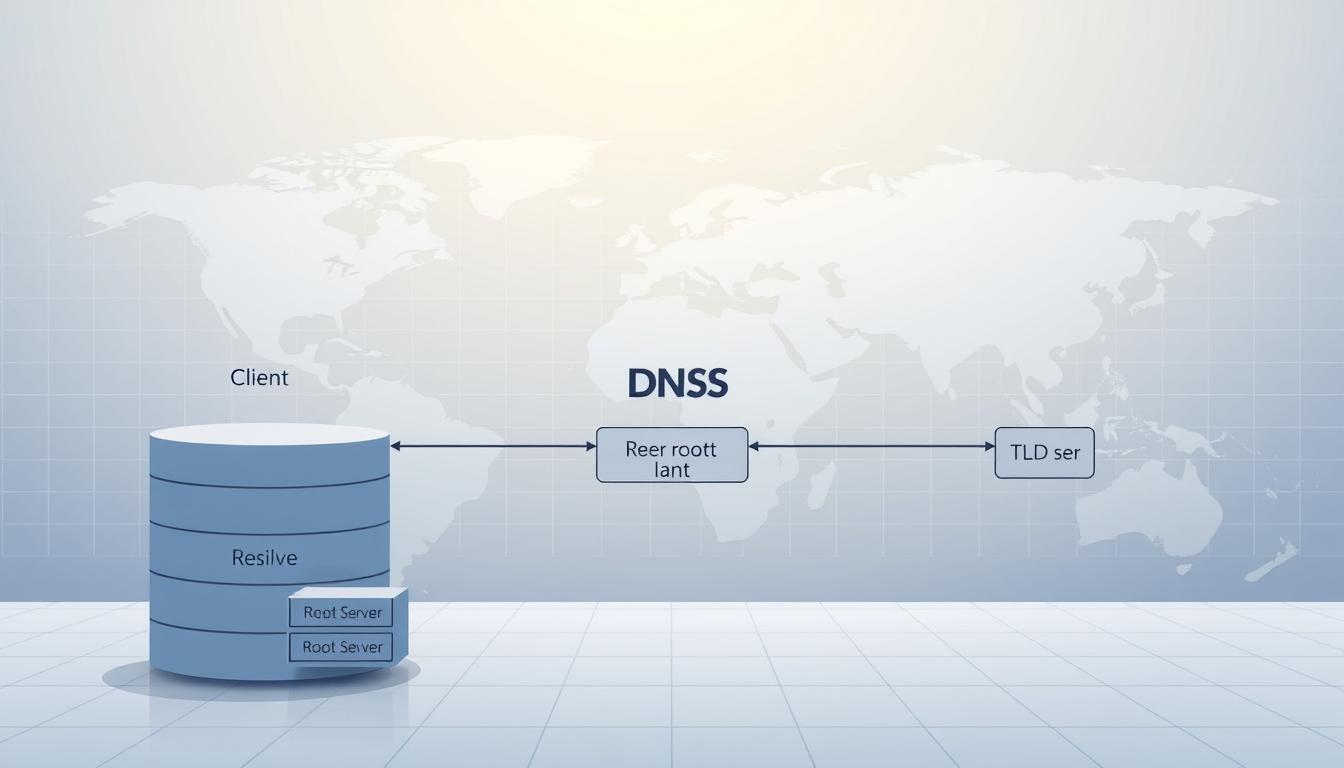
The domain name system maps human-friendly domain tags to numeric IP addresses so your browser can reach a website. This chain of lookups touches your device, a local resolver, root servers, TLD servers, and an authoritative server that returns the final address.
Public resolvers like Cloudflare 1.1.1.1 and Google Public DNS (8.8.8.8) speed queries and can block harmful sites. Caching at the OS and browser levels makes repeat visits fast by storing recent answers locally.
Originally created to replace HOSTS.TXT, the domain name system scaled the internet by adding hierarchy and delegation. In short, the system ensures every address matches a human-readable name so apps and sites work reliably.
Key Takeaways
- DNS turns readable domain labels into the numeric address your device needs to connect.
- Lookup flow: resolver → root → TLD → authoritative server delivers final records.
- Public resolvers improve speed and add security features for everyday browsing.
- Caching cuts repeated queries and speeds up site access on repeat visits.
- DNS replaced HOSTS.TXT to scale the internet and keep sites reachable.
What is DNS and why the Domain Name System matters today
Think of the internet like a giant contact list that your phone consults faster than you can dial.
The system turns a typed label into the numeric address a device needs to connect. That lets you enter www.example.com instead of memorizing 93.184.216.34. Queries travel from a resolver to root, then to TLD and an authoritative server in milliseconds. Caching at each hop speeds repeat requests and keeps pages loading fast.
From phonebooks to contact lists
Smartphone contacts removed the need to remember long numbers. The same shift happened online: friendly names map to addresses so users can browse without technical friction.
How failures break services
If a server can’t resolve a label, a website won’t load, email servers can’t route mail, and app APIs time out. Outages cascade because so many services depend on timely lookups.
- Performance: Resolvers can route you to nearby servers to reduce latency.
- Security: Filtering at resolvers helps block access to malicious sites.
- Reliability: Caching and hierarchy keep everyday traffic moving smoothly.
what is dns domain name
A clear label hides a technical trail that points your web browser to the correct server address.
People use readable domain names so they don’t memorize numeric addresses. A resolver translates that label into an IP address your device can route to. This lookup touches caches and several servers before the final answer returns.
Domain names vs. IP addresses: human-readable names and numeric addresses
A human-friendly label and a numeric address serve different roles. The label helps users; the address tells routers where to send packets. A DNS server stores mappings that link a label to a public IP so traffic reaches the correct host.
How domain names map to servers across the internet
Resolvers check local cache first. If no cached result exists, they query root, TLD, and authoritative servers to get authoritative information. Once a valid address is returned, the browser connects to an origin or CDN edge server to fetch content.
- TTL: controls how long results stay cached and cuts repeated lookups.
- Accuracy: wrong dns data misroutes traffic and breaks user sessions.
- Practical: every site visit depends on timely resolution—see the Domain Name System for more background.
How DNS resolution works in practice
A single lookup travels through several trusted tiers before your browser gets an IP address.
The lookup path: recursive resolver → root → TLD → authoritative server
The flow starts at a recursive resolver that accepts your query. If the resolver lacks a cached answer, it asks a root server for the top-level referral. The root points the resolver to the correct tld server. The tld then returns the authoritative server that holds the definitive record.
TTL and why caching speeds things up
When the authoritative server replies, the resolver stores that data for the record’s TTL. Browsers and the operating system also keep recent results in local cache to cut repeat latency.
From URL to the correct address
For most visits the resolver answers from cache, avoiding the full chain. If caches expire, the resolver runs the full lookup again and updates its cache.
For a practical deep dive into query handling and metrics, see this guide to dns resolution.
Meet the DNS servers: recursive, root, TLD, and authoritative
Specialized layers of infrastructure work together so a single query returns accurate routing data quickly.
Recursive DNS servers act for clients. They check local cache first and obey TTL values before asking others. If no cached hit exists, the resolver performs a lookup up the chain.

Root and TLD nameservers
Root hubs sit at the top and point resolvers to the right zone. There are 13 labeled root identifiers (A–M) that underpin global reachability.
TLD handlers serve their top-level zone and refer queries to the authoritative hosts for specific names.
Authoritative DNS servers
Authoritative dns servers hold the final records for a zone. The primary stores originals while secondaries replicate data for redundancy and uptime.
Registries and hosting providers run TLD and authoritative infrastructure, while ISPs and public companies operate most recursive resolvers. This separation keeps queries fast and information correct at internet scale.
- Role clarity: each layer scales specific tasks so lookups stay efficient.
- Caching: resolvers avoid extra hops when TTL permits.
- Resilience: primary/secondary authoritative setups prevent single points of failure.
DNS records and zones you need to know
Zone files group the configuration that tells resolvers how to route traffic for a label.
Each zone file starts with a global TTL and an SOA record, then lists NS and other resource records. The SOA sets authority and timing; NS entries declare which servers hold the zone. Together they form the authoritative source of routing information.
Common records and their roles
A and AAAA map a readable name to an IPv4 or IPv6 address so clients can connect to the host.
CNAME creates an alias to a canonical host. MX routes mail using priority values. TXT holds verification and SPF data, for example: v=spf1 include:_spf.mail.hostinger.com ~all.
SRV entries guide service discovery with fields for priority, weight, port, and target. PTR enables reverse lookups from an address back to a name, which helps with diagnostics and mail trust.
“Zone layout and precise record fields directly affect routing, mail delivery, and service discovery.”
| Record | Purpose | Key fields |
|---|---|---|
| A | Map to IPv4 address | TTL, IPv4 address |
| AAAA | Map to IPv6 address | TTL, IPv6 address |
| MX | Mail routing | Priority, mail server host |
| CNAME | Alias to another host | Canonical target |
Operational tip: verify TTL and SOA serials when editing a zone. Changes propagate via tld servers and resolver caches, so correct fields speed reliable updates.
Nameservers and DNS settings for your domain
Quick changes at the registrar link your site to the correct host and routing data.
Nameservers hold the records that tell the internet how to route traffic to your hosting. Providers usually publish two or more server addresses that answer queries for a zone. You must update nameservers at your registrar; if hosting and registration are separate, point the registrar to your host.
Editing settings in a control panel
Use a DNS Zone Editor to add or edit A, AAAA, CNAME, MX, TXT, and SRV records. Fill fields like Name, Points to/Target, Priority, and TTL (common default: 14400).
Propagation and verification
Changes can appear in minutes or take up to 24 hours due to caching across resolvers. Check progress with tools such as WhatsMyDNS to confirm a clean dns lookup worldwide.
“Track names and records carefully during migrations to keep a website reachable.”
| Action | Where | Notes |
|---|---|---|
| Change nameservers | Registrar | Points domain to hosting provider |
| Edit A / AAAA | Zone Editor | Set host to new IP address |
| Add MX / TXT | Zone Editor | Configure mail and verification records |
DNS queries explained: recursive, iterative, and non-recursive
Resolvers and upstream servers use distinct query styles to balance speed with authority.
Recursive queries run between a client and a recursive resolver. The resolver must return either an answer or a clear error. That forces the resolver to chase records across the hierarchy until it succeeds or fails.
Iterative queries occur between resolvers and nonlocal servers like root, TLD, or authoritative hosts. Those servers usually reply with referrals rather than full answers. Referrals point the resolver to the next server that likely holds the requested data.
Non‑recursive queries happen when the resolver already has a valid answer in cache. The resolver returns the record immediately, enabling a fast dns lookup without extra hops.
- Recursive queries guarantee a final answer for clients or a clear error.
- Iterative queries let servers refer resolvers onward to save work.
- Non‑recursive queries speed common lookups using cached information.
Practical example: a resolver tries cache first (non‑recursive). If missing, it asks upstream servers iteratively. If asked by a client, the resolver performs recursion and returns the final data. Recognizing these patterns helps diagnose resolution behavior in the field.
Caching and the DNS cache on your device and resolver
Caches keep recent lookup answers close to the user so pages open faster.
Where caching happens: Browsers, the operating system, local dns on the device, and an upstream resolver all store records to avoid repeated lookups.
Each layer holds data for the TTL set by the zone owner. Short TTLs speed updates but increase query load. Longer TTLs cut traffic and help performance.
When to flush cache: If a site resolves to the wrong address after changes, or connectivity fails, clear local caches first. On Windows run ipconfig /displaydns to view entries and use flush to remove stale items.
Avoid overly aggressive TTL reduction during normal ops. Balanced values like 14400 seconds (4 hours) give a good mix of speed and freshness.
Quick reference
| Layer | Stored items | When to flush |
|---|---|---|
| Browser | Recent lookups, session records | After site IP change or errors |
| Operating system | Cached resource records | Display cached list, then clear if stale |
| Resolver | Authoritative replies per TTL | When global changes don’t appear |
“Clearing the right cache often restores connectivity without waiting for global propagation.”
Security essentials: from DNSSEC to stopping malicious sites
Cryptographic checks and infrastructure hardening together raise the cost for attackers.
DNSSEC adds cryptographic signatures to responses so resolvers can verify origin and integrity. Availability varies by registrar and provider, but enabling it prevents forged answers from reaching clients. Signed records protect users by making tampering detectable as responses travel across the internet.
The threat landscape includes cache poisoning that misdirects traffic, amplification attacks that overload a server, tunneling that smuggles data, and hijacking or subdomain takeover that seizes control.
Layered defenses and hardening
- Enable DNSSEC where supported and sign sensitive records.
- Deploy redundancy and anycast to spread load and improve resilience.
- Apply rate limiting to blunt volumetric abuse and protect recursive dns endpoints.
- Require two‑factor authentication at registrars and restrict control panels.
- Monitor health, audit zone records regularly, and flush caches after major changes.
“Resolver policies that block malicious sites and curated threat feeds add practical protection for users.”
Operational choices in dns settings—like strict TTLs for critical records and routine health checks—reduce exposure and speed recovery during incidents. Together, cryptographic validity, robust infrastructure, and active monitoring keep queries honest and services available.
Public, private, and managed DNS services
Managed providers bundle global reach and operational guarantees so teams avoid running complex infrastructure themselves.
Public recursive services offer free resolvers anyone can use for faster lookups and added filtering. Examples include Cloudflare (1.1.1.1), Google Public DNS (8.8.8.8), and Quad9. These recursive dns endpoints are trusted for speed and privacy features.
Private authoritative setups
Organizations host authoritative dns servers inside their network to protect internal records and names. These private hosts sit behind firewalls and serve internal tld and record data only to authorized clients.
Managed DNS offerings
Managed services add SLAs, anycasted footprints, health checks, APIs, DNSSEC, GSLB, and DDoS mitigation. Providers speed propagation and give tooling for monitoring and automation.
“Match your choice to staffing, scale, and latency goals to balance control against operational risk.”
- Run your own authoritative layer for tight control and sensitive internal records.
- Choose a managed provider to gain global resilience and simplified ops.
Hands-on: DNS lookup, troubleshooting, and performance tips
A quick lookup often reveals whether an outage stems from local cache, an upstream resolver, or the authoritative hosts.
DNS lookup tools: NSLOOKUP, WHOIS/RDAP, and online checkers
NSLOOKUP lets you request specific record types and query an explicit resolver to compare answers.
WHOIS/RDAP returns registrar details and published nameservers so you can verify delegation for a top-level domain.
Use global checkers like WhatsMyDNS to confirm propagation across regions and to spot inconsistent records on multiple servers.
Fixing “DNS server isn’t responding” and common misconfigurations
Start with connectivity: reboot the client, test another network, and inspect the operating system cache with ipconfig /displaydns.
If entries look stale, flush local cache and try again. Next, update client settings to a known public resolver and retest queries.
Verify zone health at the registrar and ensure NS and SOA entries match the authoritative hosts. Fix wrong record targets or missing delegation to restore reachability.
Optimizing performance: TTL tuning, secondary DNS, and multi-region
Set balanced TTLs to speed updates without overloading servers. Short TTLs help rapid failover; longer values improve cache hit rates.
Deploy secondary DNS for failover and anycast authoritative servers across regions to cut latency to the nearest server.
Measure changes by timing lookups before and after edits and by validating the authoritative answer for each record. That confirms both latency and accuracy of dns data.
“Trace queries across referrals from root to authoritative to ensure delegation is correct and failures are isolated.”
Conclusion
A healthy resolution setup combines clear records, proper delegation, and monitoring to keep services reachable.
DNS underpins every website visit, email delivery, and API call by turning readable names into a routable address.
Keep vital zone entries accurate, enforce registrar protections like 2FA, and enable DNSSEC where supported. Use public or managed resolvers for faster, more secure queries and add redundancy across authoritative servers.
Operational checks—NSLOOKUP, WHOIS/RDAP, cache inspection, and propagation tools—help spot issues fast. Good stewardship of records and delegation lowers outage risk and speeds recovery.
Apply these practices and your infrastructure will serve users reliably, with better performance and stronger protection.
FAQ
What is the Domain Name System and why does it matter today?
The Domain Name System converts human-friendly addresses into numeric IP addresses so browsers, email servers, and apps can find hosts on the internet. Without this translation layer, people would need to remember long IP strings instead of easy-to-read labels, and outages or misconfigurations would block websites and mail services worldwide.
How do domain names differ from IP addresses?
Domain labels are readable identifiers like example.com, while IP addresses are numeric routes used by routers and servers. A mapping record (A for IPv4 or AAAA for IPv6) links a label to its machine address so clients can connect to the correct host.
How does a typical resolution path work from a browser to an address?
When you enter a URL, the browser asks a recursive resolver. If the resolver lacks a cached answer, it queries a root server, then a TLD server, then the authoritative server for the zone. The authoritative server returns the record, and the resolver sends the IP back to the browser so the connection can start.
What role do recursive resolvers play?
Recursive resolvers act as intermediaries that perform full lookups on behalf of clients. They cache results to speed future queries and reduce load on upstream servers. Public examples include Cloudflare 1.1.1.1 and Google Public DNS.
What are authoritative servers and why are they important?
Authoritative servers hold the definitive zone data for a domain, including SOA, NS, A, MX, and TXT records. They answer queries with the official information; if authoritative data is wrong, visitors and mail systems will be misdirected.
How do TTL and caching affect DNS changes?
Time to live (TTL) tells resolvers how long to keep a record in cache. Low TTLs make updates propagate faster but increase query load. High TTLs reduce load but delay visible changes. Propagation delays often reflect cached answers held by many resolvers.
Which record types should I know for everyday administration?
Key records include A and AAAA (address mapping), CNAME (alias), MX (mail exchange), TXT (verification), SRV (service locations), PTR (reverse mapping), SOA (zone authority), and NS (delegation). Each serves a clear operational purpose for hosting, mail, and verification.
Where do I change nameservers and DNS settings for my domain?
Update nameserver delegation at your domain registrar. For record edits, use the DNS zone editor provided by your registrar or hosting provider, or manage records via an API if you use a managed DNS service with global anycast.
What are iterative and non-recursive queries?
Iterative queries return the best available referral (for example, a TLD server) and let the client continue the lookup. Non-recursive queries ask an authoritative server for data it already holds. Recursive queries ask a resolver to complete the entire lookup and return the final answer.
When should I flush local caches on a device or resolver?
Flush caches after making DNS changes that don’t appear, or if you suspect stale or poisoned entries. Browsers, operating systems, and recursive resolvers each maintain caches that might need clearing to see fresh records.
How does DNSSEC protect DNS data?
DNSSEC adds digital signatures to zone records so resolvers can validate authenticity and integrity. This prevents attackers from spoofing records or redirecting traffic, though adoption requires proper signing of zones and resolver validation.
What common DNS threats should administrators monitor?
Watch for cache poisoning, DDoS amplification using open resolvers, DNS hijacking, and tunneling abuses. Mitigations include rate limiting, restricting recursion, implementing DNSSEC, and running redundant authoritative services with anycast.
What options exist for managed, public, and private DNS services?
Public recursive providers (Cloudflare, Google Public DNS, Quad9) handle client resolution. Managed DNS vendors offer SLAs, global anycast, and traffic tools. Private authoritative systems serve internal networks and should run separately from public zones for security.
Which tools help with lookup and troubleshooting?
Utilities like nslookup, dig, and online DNS checkers reveal records and trace resolution paths. WHOIS or RDAP show registrar and registration data. Use these tools to diagnose “server not responding” errors and misconfigurations.
How can I improve DNS performance and resilience?
Use secondary authoritative servers, tune TTLs sensibly, enable anycast for global low-latency responses, distribute services across regions, and monitor query patterns. These steps reduce latency and improve uptime during peak load or attacks.
What is reverse DNS and when is it needed?
Reverse DNS maps IP addresses back to labels using PTR records. Mail servers and some security checks use reverse lookups to validate sender hosts, so correct PTR entries improve deliverability and reputation.